Enhancing Performance of Asynchronous Data Traffic over the Bluetooth Wireless Ad-hoc Netwo

Enhancing Performance of Asynchronous Data Traf?c over the Bluetooth Wireless Ad-hoc Network Abhishek Das,Abhishek Ghose,Ashu Razdan,Huzur Saran&Rajeev Shorey
IBM India Research Laboratory,
Block1,Indian Institute of Technology,
Hauz Khas,New Delhi110016,India
Email:srajeev@https://www.sodocs.net/doc/d36894292.html,
Phone:91-11-6861100;Fax:91-11-6861555
Abstract—Emerging technologies such as Bluetooth are expected to be-come a ubiquitous solution for providing short range,low power,low cost, pico-cellular wireless connectivity.Bluetooth is a Master driven Time Divi-sion Duplex(TDD)system that supports an asynchronous channel for data traf?c as well as synchronous channels for voice traf?c.Data applications running over Bluetooth such as http,ftp and real audio will need transport layer protocols such as TCP and UDP to send packets over the wireless links.In this paper we study several schemes designed to improve the per-formance of asynchronous data traf?c over a Bluetooth piconet that sup-ports multiple active slaves.We propose and compare a number of SAR policies and MAC scheduling algorithms with a view towards enhancing the performance of transport layer sessions.We investigate the effect of different FEC and ARQ schemes at the baseband level,using a two-state Markov channel model for the Bluetooth RF link.We also study how the presence of circuit-switched voice impacts the performance of data traf?c.
Keywords—Medium Access Control(MAC),Scheduling,Time Division Duplex(TDD),Segmentation and Reassembly(SAR),Forward Error Cor-rection(FEC),Automatic Repeat Request(ARQ),TCP,UDP.
I.I NTRODUCTION
Bluetooth technology[1],[2]allows for the replacement of the numerous proprietary cables that connect one device to an-other with a universal short-range radio link.Beyond untether-ing devices by replacing cables,Bluetooth provides a universal bridge to existing data networks,a peripheral interface,and a mechanism to form small private ad-hoc groupings of connected devices away from?xed network infrastructures.
Bluetooth has a number of distinctive features compared to existing wireless LANs such as:
Support for both data and voice traf?c
Frequency hopping to avoid interference
A master driven Time Division Duplex(TDD)system at
the Medium Access Control(MAC)layer to support full duplex transmission
Segmentation and Reassembly(SAR)to handle large data packets
Support for link level Automatic Repeat Request(ARQ) and Forward Error Correction(FEC)schemes
Abhishek Das and Ashu Razdan are in the Computer Science and Engineer-ing Department,Indian Institute of Technology at Kharagpur and Guwahati,re-spectively.Abhishek Ghose is in the Electrical Engineering Department,Indian Institute of Technology,Mumbai,India.Dr.Huzur Saran is a Professor in the Department of Computer Science and Engineering,Indian Institute of Technol-ogy,New Delhi,India.He is currently on a sabbatical at Stanford University, CA,USA.Email:saran@cse.iitd.ernet.in;Dr.Rajeev Shorey is a Research Staff Member in the IBM India Research Laboratory,New Delhi,India.This work was done while the?rst three authors were summer interns in the IBM India Research Laboratory,New Delhi from May to July’2000.
These key features of Bluetooth will signi?cantly impact the performance of data traf?c over Bluetooth.Fragmentation of large data packets by performing SAR,which allows them to be transmitted in small baseband packets,may increase their end-to-end delay.Master driven scheduling at the MAC level will affect throughput and queueing delay.The success rate of data transmissions will be affected by the presence of FEC and ARQ mechanisms at the link level.The bandwidth available for data traf?c will be reduced in the presence of voice connections.The effect of these issues needs to be better understood in order to enhance the performance of asynchronous data traf?c over Blue-tooth.
Since TCP[3]is the most widely used transport protocol for reliable data services over the Internet,our primary focus in this paper is on the performance of TCP over Bluetooth.A key ob-servation for wireless environments is that since TCP interprets packet loss as a sign of congestion and cuts back its window,its performance may deteriorate in the presence of random losses that cannot be attributed to congestion[4].Considerable atten-tion is being given to the design of a better TCP over the wireless link[5],[6].Since Bluetooth is distinct from existing wireless LANs,these studies are not directly applicable to Bluetooth.We also study the performance of Constant Bit Rate(CBR)applica-tions using UDP,a minimal non-guaranteed datagram service without any?ow control or congestion avoidance.
In this paper,we propose two SAR policies with the aim of increasing link utilization and decreasing end-to-end delay of data packets.When multiple data transfers share the wireless link,as in a Bluetooth piconet,MAC scheduling algorithms are needed to achieve fair sharing of bandwidth,high link utilization and low queue occupancy.We demonstrate that Round-Robin scheduling is unable to meet these requirements and propose three new scheduling algorithms which meet these criteria ad-equately.We also incorporate Channel State Dependency[7] in these algorithms in order to improve the performance in the presence of bursty wireless errors.In accordance with observa-tions reported in earlier studies of packet loss behavior in wire-less LANs[5],[6],[18],a two state Markov model has been used to model the errors in the wireless channel.Bluetooth pro-vides support for error correction at the link level through FEC and ARQ schemes.We investigate the performance improve-ment provided by FEC and ARQ schemes.We also compare the performance of different versions of TCP,namely,Tahoe,Reno, New Reno and Sack[3],[8]over Bluetooth.
Prior research closest to our work is that of Johansson et
[9].They address the performance of TCP/IP over a wireless network but with very simplistic assumptions. assume only two nodes(master and slave)in a Bluetooth conet and study the behavior of TCP Vegas.Further,the model bit errors with a constant loss probability.They do assume any FEC for data traf?c arguing that doing so will largest ideal throughput.They do not specify any ARQ
at the baseband level to prevent packet loss.In[10],the thors have analysed and compared the behaviour of three dif-ferent scheduling algorithms for Bluetooth:strict round polling,exhaustive polling and fair exhaustive polling. study average delay versus bitrate for the three scheduling gorithms.The authors have demonstrated an increase in per-formance(high throughput and low delays)when allowing packets to be sent in multi-slots(i.e.,3or5slot baseband
ets).The simulation study uses very simplistic assumptions:(i) the packet loss probability is constant for all packets,(ii)the master does not send any traf?c to the slave but just forwards traf?c from one slave to another,(iii)the buffers are assumed to be unbounded.Kalia et al[11]have proposed some simple SAR policies and MAC scheduling algorithms for Bluetooth. They propose two scheduling policies that utilize information about the size of the Head-of-the-Line packet at the master and slave queues to schedule the TDD slots effectively.These poli-cies achieve high throughput and greater fairness compared to the Round-Robin based scheduling policies.The work in[11] is restricted only to the link layer and hence is not optimized for transport layer sessions.
The remainder of this paper is organized as follows.Section II gives a brief introduction to the Bluetooth technology.In Sec-tion III,we propose SAR and MAC scheduling policies and also discuss other important design issues in Bluetooth which affect the performance of asynchronous data traf?c.The simulation model is presented in Section IV.In Section V,we present our simulation results and analyses.Finally,we conclude by pre-senting a summary of our results and some suggestions for fu-ture work in Section VI.
II.B LUETOOTH T ECHNOLOGY
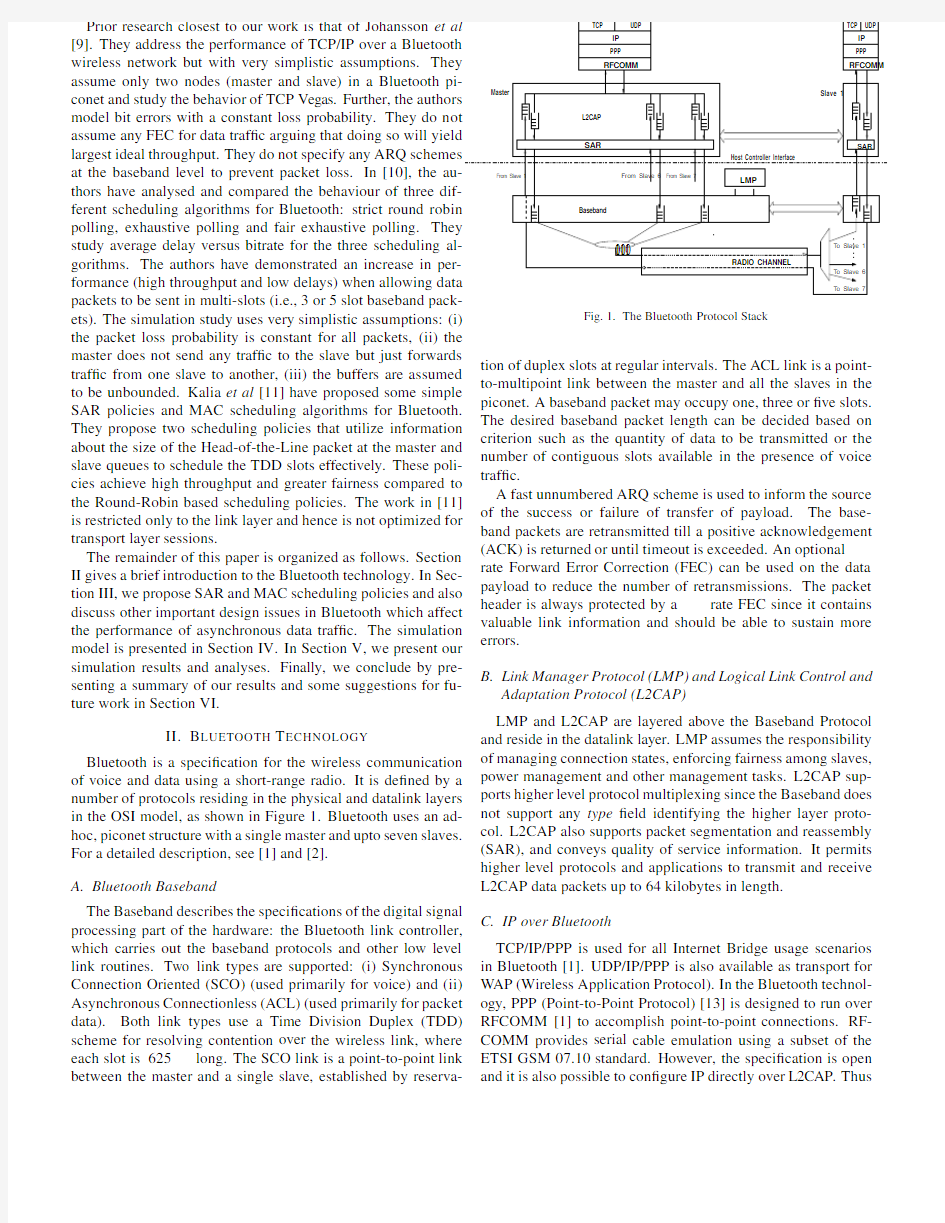
Bluetooth is a speci?cation for the wireless communication of voice and data using a short-range radio.It is de?ned by a number of protocols residing in the physical and datalink layers in the OSI model,as shown in Figure1.Bluetooth uses an ad-hoc,piconet structure with a single master and upto seven slaves. For a detailed description,see[1]and[2].
A.Bluetooth Baseband
The Baseband describes the speci?cations of the digital signal processing part of the hardware:the Bluetooth link controller, which carries out the baseband protocols and other low level link routines.Two link types are supported:(i)Synchronous Connection Oriented(SCO)(used primarily for voice)and(ii) Asynchronous Connectionless(ACL)(used primarily for packet data).Both link types use a Time Division Duplex(TDD) scheme for resolving contention over the wireless link,where each slot is625long.The SCO link is a point-to-point link between the master and a single slave,established by reserva-
Fig.1.The Bluetooth Protocol Stack
tion of duplex slots at regular intervals.The ACL link is a point-to-multipoint link between the master and all the slaves in the piconet.A baseband packet may occupy one,three or?ve slots. The desired baseband packet length can be decided based on criterion such as the quantity of data to be transmitted or the number of contiguous slots available in the presence of voice traf?c.
A fast unnumbered ARQ scheme is used to inform the source of the success or failure of transfer of payload.The base-band packets are retransmitted till a positive acknowledgement (ACK)is returned or until timeout is exceeded.An optional rate Forward Error Correction(FEC)can be used on the data payload to reduce the number of retransmissions.The packet header is always protected by a rate FEC since it contains valuable link information and should be able to sustain more errors.
B.Link Manager Protocol(LMP)and Logical Link Control and
Adaptation Protocol(L2CAP)
LMP and L2CAP are layered above the Baseband Protocol and reside in the datalink layer.LMP assumes the responsibility of managing connection states,enforcing fairness among slaves, power management and other management tasks.L2CAP sup-ports higher level protocol multiplexing since the Baseband does not support any type?eld identifying the higher layer proto-col.L2CAP also supports packet segmentation and reassembly (SAR),and conveys quality of service information.It permits higher level protocols and applications to transmit and receive L2CAP data packets up to64kilobytes in length.
C.IP over Bluetooth
TCP/IP/PPP is used for all Internet Bridge usage scenarios in Bluetooth[1].UDP/IP/PPP is also available as transport for W AP(Wireless Application Protocol).In the Bluetooth technol-ogy,PPP(Point-to-Point Protocol)[13]is designed to run over RFCOMM[1]to accomplish point-to-point connections.RF-COMM provides serial cable emulation using a subset of the ETSI GSM07.10standard.However,the speci?cation is open and it is also possible to con?gure IP directly over L2CAP.Thus
two scenarios can be envisaged:
1.TCP/IP running over PPP over RFCOMM,which is lay-
ered over L2CAP.This enables smooth operation and inter-operability with legacy applications.In this case,the fram-
ing information available through HDLC(Higher Level Data Link Control)in PPP should be passed to the L2CAP layer to make it aware of PPP packet boundaries,thus en-abling ef?cient SAR[14].
2.TCP/IP layered directly over L2CAP.
The second approach has lesser overheads[14]and is used in our simulation model.However,our results also apply to the former case since the overheads due to RFCOMM and PPP headers(14 bytes)are negligible compared to the size of the TCP packet and the delay involved is a constant factor.
III.D ESIGN I SSUES IN B LUETOOTH
In this section,we examine some of the design issues which have a signi?cant impact on the performance of asynchronous data traf?c over Bluetooth.
A.Segmentation and Reassembly schemes
Segmentation and reassembly(SAR)mechanisms are used to improve ef?ciency by supporting a maximum transmission unit (MTU)size larger than the largest baseband packet.This re-duces overheads by spreading the packets used by higher layer protocols over several baseband packets,each covering1,3or5 slots.It is important to note that the payload size(without FEC) for a5slot packet(339bytes in5slots or67.8bytes/slot)is sig-ni?cantly larger than that of3slot packets(183bytes in3slots or61bytes/slot)and1slot packets(27bytes/slot).We de?ne slot
limit may be less than5due to presence of SCO connections or due to a very high bit error rate in the wireless channel.This parameter can be conveyed by the LMP to the L2CAP through a signalling packet.We now propose two SAR schemes.
A.1SAR-Best Fit(BF)
This algorithm aims to reduce the wasted bandwidth in the baseband packets and uses a best-?t method to segment the higher layer packets.The algorithm can be summarized in the following steps:
1.If
,divide the remaining bytes into an inte-gral number of3slot baseband packets.
3.Divide the remaining bytes into an integral number
of1slot baseband packets.
For example,consider an L2CAP packet of size556bytes and
Initial000
010
Step2102
21-
Step4---
---
,divide the L2CAP packet into an inte-gral number of5slot baseband packets.
2.If the size remaining to be fragmented is larger than that of a3slot packet,send it as a5slot packet.
3.If
ing achieves fair sharing of bandwidth and high link utilization when each such connection has equal data?ow.In a typical situation,however,each slave in the piconet has varying data input rates.Consequently,numerous baseband slots are wasted by polling sources with low input rate,thereby decreasing link utilization,increasing queueing delay and leading to unfair shar-ing of bandwidth.To address these issues,we propose three scheduling algorithms,which incorporate the following meth-ods:
1
S
S2
S3 S4 S5 S6 S7
S2
S3
S6
S7
S5
S4
1
S
Transmit
Receive
Bluetooth MAC
Per Destination Queues
Master
Scheduler
Link State
Monitor
Slaves Fig.2.MAC Scheduling in Bluetooth
Queue Priority based on Flow Bit:Per-slave baseband queues at the master and similar queues at the slave are maintained(as shown in Figure2).We assign priority to these queues based on the pending data in the corresponding L2CAP buffers,and use the?ow bit present in the payload header?eld of the baseband packet for this purpose.This?ow bit is used to convey?ow information at the L2CAP level as intended in the Bluetooth speci?cation[1].It is set when the number of packets in the L2CAP buffer for a particular slave is larger than a threshold buf
)for each queue having the?ow parameter set.
Based on these ideas,we propose the following scheduling al-gorithms:
C.1Adaptive Flow-based Polling(AFP)
Polling interval for a particular slave is de?ned as the maxi-mum time limit,before which it must be served by the master and is decided based on QoS requirements.We de?ne to be the polling interval negotiated during master-slave connec-tion setup.We assume a homogeneous situation initially where all the slaves have the same value of.AFP uses an adaptive polling interval,whose value is changed based on the traf?c rate in the wireless channel as indicated by the variable.
1.If and the Head-of-Line(HOL)packet is a data
packet,transmit the data packet and set the polling interval
to.In this case,there is a high?ow rate for this slave, and hence its polling interval is reduced so that it can be served more frequently.
2.If and the HOL packet is a data packet,transmit
the data packet and keep the polling interval unchanged.
3.If a poll packet is transmitted and a null packet is received,
double the current polling interval unless a threshold value is reached.The polling interval is increased so as to reduce slots wasted when neither the master nor the slave have any data to transmit.
C.2Sticky
Each slave is serviced in a cyclic fashion contingent on the state of:
1.If,a maximum of num
sticky is a variable param-eter greater than one,whose optimal value is found through simulations in Section V-C.
2.If,one packet is transmitted for that queue,as
in Round-Robin scheduling.
C.3Sticky Adaptive Flow-based Polling(StickyAFP)
This is similar to AFP except that when and the HOL packet is a data packet,a maximum of num
. The purpose of the FEC scheme on the data payload is to reduce the number of retransmissions.However,in a reasonably error-free environment,FEC results in unnecessary overhead that re-duces the https://www.sodocs.net/doc/d36894292.html,ing a two state Markov channel model (described in Section IV-A)in our simulations,we study the ef-fect of using FEC on the baseband payload and of varying the parameter
independent[7],[16],packets for other slaves could be success-fully transmitted during this interval.We propose Channel State Dependent Packet(CSDP)scheduling[7]versions of our algo-rithms to improve the data throughput over lossy wireless links. Upon encountering a packet loss(indicated by receipt of a nega-tive ACK),CSDP policies defer the retransmissions to that slave till the next polling instant.If the deferred period length is more than TCP’s timeout period,the source will timeout and retrans-mit a copy of the delayed packet,thereby unnecessarily increas-ing the load on the system.In practice,however TCP’s timeout period is of the order of seconds,while the duration of burst periods is of the order of milliseconds.This time difference is suf?cient for link layer mechanisms to attempt loss recovery by retransmission over the radio link.We compare the performance of CSDP-AFP,CSDP-Sticky and CSDP-StickyAFP through sim-ulations in Section V-D.
E.Number of SCO connections
Upto three simultaneous SCO links for supporting real-time traf?c,such as voice,can be supported by the master.The mas-ter will send SCO packets at regular intervals,the so-called SCO intervals(counted in slots)in the reserved master-to-slave slots.The SCO slave is always allowed to respond with an SCO packet in the following slave-to-master slot.
Since SCO links reserve slots,no ACL packets can be sup-ported in the presence of three SCO links.In the presence of two SCO links,only1slot ACL packets can be sent.In the presence of one SCO link,1and3slot ACL packets can be sup-ported.The performance of data(ACL)traf?c in the presence of varying number of SCO links is described in Section V-E. F.TCP variants
Current implementations of TCP,namely TCP Tahoe and TCP Reno[8],use an acknowledgement number?eld that con-tains a cumulative acknowledgement,indicating that the TCP receiver has received all of the data upto the indicated byte.A selective acknowledgement option allows receivers to addition-ally report non-sequential data they have received(implemented in Sack TCP[8]).New-Reno[8]avoids many of the retransmit timeouts of Reno without requiring SACK.Through simulations in Section V-F,we compare the performance of TCP Tahoe and Reno with two modi?ed versions of TCP Reno:TCP New Reno and TCP Sack.
IV.S IMULATION M ODEL
We have developed an extensive simulation model for Blue-tooth,using the Network Simulator()[15]and the MATLAB package,containing the core Bluetooth protocol layers(shown in Figure1)as well as TCP/IP.The network is modeled as a Bluetooth piconet with one master and seven slaves.
The traf?c sources shown in Figure3generate TCP/UDP traf?c which is transmitted to the transport layer.After the TCP/UDP header is added,the packets are sent to the network layer.The L2CAP layer receives data segments from the upper layer,adds an L2CAP header and enqueues them in the L2CAP https://www.sodocs.net/doc/d36894292.html,rge L2CAP packets are then segmented into multi-ple smaller baseband packets by a SAR module at the L2CAP and are enqueued in a baseband https://www.sodocs.net/doc/d36894292.html,ing a MAC schedul-ing algorithm,the packets are then sent at appropriate intervals through the physical RF link.This is modeled in Section IV-A. When the slave’s baseband layer receives a packet,it is en-queued in the baseband buffer and then sent to the SAR mod-ule in L2CAP for reassembly.The reassembled packets are transmitted upwards through the protocol stack to the transport layer.TCP then sends an ACK for correctly received packets (UDP does not send any ACKs).In our simulations,we use a TCP/UDP Packet size of512bytes and a TCP ACK size of40 bytes.
The actual traf?c sources may be located at any point in the Internet.However,as the bandwidth associated with wireline networks is much higher than is available in the Bluetooth wire-less link,the latter becomes a bottleneck.Thus,for the purpose of our simulation,we may equivalently place our sources at the master and account for the wired part of the network by a con-stant delay.In the simulated network(see Figure3),slaves1and 2have persistent TCP(ftp)connections which are active from0 to60and10to20seconds respectively.Slaves3to7receive CBR traf?c running over UDP with rates ranging from5520bps to17664bps,as shown in Figure3.Note that we have tried to capture a variety of traf?c sources in the traf?c model,which is evident from the choice of?ows.While we study this traf?c model,we look into the effect of all sources rather than a single one and hence we use the performance metrics of link utiliza-tion,average throughput and average end-to-end delay which re?ect the overall data performance rather than the performance of a single slave in a piconet.
We have used TCP-Reno[8]in our simulations since it is one of the most common reference implementations for TCP.
Slave 1
Slave 2
Slave 3
Slave 4
Slave 5
Slave 6
Slave 7
Fig.3.Traf?c Sources used in Simulation
Performance Metrics
We study three performance metrics:throughput,end-to-end delay and link utilization.Throughput is an indication of how much data the user can receive per second.In our simulation results,the throughput is averaged every0.5seconds.We de?ne End-to-end delay of packets to be the delay incurred from the time it is enqueued in the transport layer buffer to when it is re-ceived.Note that this includes the queueing delay at the buffers. Link Utilization quanti?es how much of the available bandwidth is actually being used by baseband packets.
A.Correlated Fading Channel Model
Since packet-error rates critically depend on the distance
tween the transmitter and receiver [17],the wireless varies with each user,depending on their location.For speed radio transmissions at a high carrier frequency,as in tooth (1Mb/s at 2.4GHz),the fade durations are comparable transmission times of TCP packets [5]and hence,packet cannot be modeled as being independent of each other.ever,the frequency-hopping scheme,incorporated in the tooth radio,leads to considerably smaller bursts of errors pared to other wireless links.In accordance with common
tice,we model the Bluetooth RF link as a discrete two-state Markov Chain [5],[6],[18]as illustrated in Figure 4.Since wireless channels have been shown to be distinct and time-varying for each user [16],we associate independent Markov channel models with each master-slave connection.At any point
μμB
G
B
Fig.4.Transition Structure of the Markov Loss Model
of time,we model the channel as being in one of the two states,(Good)with BER or (Bad)with BER .These BER values are dependent on the tics of the propagation environment and the transmission lation scheme.The mean residency time in states with high Error Rate (BER)are longer than a single packet time,resulting in correlated packet losses.We assume that time spent in each state is exponentially distributed,with ferent mean values,that is,different rates of state transitions and .According to the properties of exponentially random variables,the average time between state transitions be expressed by
and .To obtain average parameter values of the indoor radio vironment,time-varying channel impulse responses were simu-lated using a wide band channel model.As GFSK is used in the Bluetooth Radio,GFSK BER vs results are taken from [20].We take a log-normal distribution for the received signal amplitudes as it provides the closest ?t for indoor wireless ra-dio environments [21].The two states of the Markov model are constructed by partitioning the envelope of the received signal into two intervals,and thus determine the mean residency times and BERs of the two states.The parameter values obtained are
,,ms and
ms.
Note that the objective in this paper is to illustrate the be-havior of a transport session when packets are subject to bursty
losses.An approximate characterization of the wireless channel is suf?cient to illustrate these effects.
Fig.5.TCP throughput vs time [slot
limit =5]
Fig.7.Link utilization vs time [slot
Buffer Size
A v e r a g e T C P t h r o u g h p u t (k b /s )
Fig.8.Average TCP throughput vs L2CAP Buffer Size
using
or ,both SAR-BF
and SAR-OSU will fragment the 556byte L2CAP packet into the same number of baseband packets,and hence there will not be any appreciable difference in their performance.Due to the superior performance of SAR-OSU,it is used for the remaining simulations in this paper.
B.L2CAP Buffer size
In this section,we use Round-Robin scheduling and assume an error-free channel to isolate the effect of buffer size on TCP performance.In Figure 8,we plot the average TCP through-put as a function of buffer size for a persistent TCP connection (to Slave 1)as well as for a short TCP transfer (to Slave 2)for
.This gives a bandwidth-delay product equiv-alent to 4.4packets,which is quite close to 5.This reasoning,however,is approximate since the entire 1Mb/s bandwidth of the radio link is not available to a single connection.
From Figure 8,it is also observed that the throughput perfor-mance with
which is in turn better than that for
in the Sticky algorithm is compared
with that of the Adaptive Flow-based Polling (AFP)and Round-
Time (seconds)
T C P t h r o u g h p u t (k b /s )
Fig.12.Link utilization for scheduling algorithms
Robin (RR)algorithms.From this graph,we clearly observe that the AFP and Sticky algorithms give signi?cantly improved per-formance compared to RR.The throughput of Sticky increases with increase in the value of
value of 16.
In Figure 11,the TCP throughput of AFP is compared to that of StickyAFP for
value of 16is better than that of AFP and Stick-yAFP for a
value of 16is not very signi?cant.
In Figure 12,the link utilization under different scheduling al-gorithms is compared.From the graph,we see that high link uti-lization is obtained for StickyAFP (
)and AFP,as compared to Round-Robin.
In Figure 13,the average end-to-end delay is plotted for each of the slaves under different scheduling algorithms.The Sticky algorithm is found to have the lowest end-to-end delay while StickyAFP has the highest.By increasing the polling interval for those queues that have less data,AFP decreases the num-ber of poll packets which otherwise cause underutilization of available bandwidth,and hence increases link utilization.Sticky reduces queue occupancy by transmitting multiple packets con-secutively from queues with a high backlog,hence preventing
Fig.13.End-to-end delay for scheduling algorithms
times.
Although AFP,StickyAFP (
)give the best results in terms of link utiliza-tion as well as throughput (to Slave 1),we observe that Stick-yAFP leads to signi?cantly higher end-to-end delay.Thus we infer that AFP and Sticky (with a high value of
(maximum num-ber of retransmissions of baseband packets)under AFP and CSDP-AFP in the presence and in the absence of a 2/3rate FEC.The corresponding values for AFP in an error free chan-nel are also plotted for comparison.These ?gures clearly indi-cate the performance degradation in the presence of errors,as well as the additional reduction in link utilization and increase in end-to-end delay due to the use of FEC.A remarkable ob-servation is that when FEC is added,the performance is inde-pendent of
,the performance does not vary signi?cantly.
This motivates us to choose the optimum value of
tx_thresh
A v e r a g e E n d -t o -e n d d e l a y (s e c o n d s )
Fig.15.End-to-end delay vs tx
thresh for CSDP algorithms
Figure 16clearly illustrates that the CSDP versions of
proposed scheduling algorithms do not give a signi?cant perfor-mance improvement and their relative performance is the same as that in the error-free channel condition.Since the burst
ror periods in the wireless channel are short enough to allow packets to be successfully retransmitted before
(1and 3)are possible.The graphs
show that a higher throughput and lower end-to-end delay is ob-tained for .Further,for one SCO connection,a lower throughput and higher end-to-end
delay is obtained for
than for .This is ex-pected since for a larger
,more slots are available for ACL packets.Further,as shown in the graphs,the highest throughput and lowest end-to-end delay is obtained for AFP with no voice connections.
Fig.17.Throughput degradation in the presence of voice
Fig.18.End-to-end delay in the presence of voice
Fig.19.Performance of TCP Versions
F .TCP variants
The performance of the different TCP versions in the pres-ence of errors,for the TCP connection to slave 1,is shown in Figure 19.NewReno performs marginally better than the other versions.However,the difference in throughput is insigni?cant which clearly illustrates that the ef?cient link layer ARQ scheme of Bluetooth eliminates the need for modi?cations at the trans-port layer for error recovery.
VI.C ONCLUSION AND F UTURE W ORK
We have presented methods to enhance the performance of asynchronous data traf?c over a Bluetooth piconet with a master and seven active slaves.We have used both TCP and UDP traf-?c sources in our study.To begin with,we proposed two new SAR mechanisms:SAR-BF and SAR-OSU,that increase the link utilization and throughput,as well as reduce the end-to-end packet transmission delays.SAR-OSU outperforms SAR-BF in all respects,i.e.,throughput,link utilization and packet trans-mission delays.Further,we demonstrated that an L2CAP buffer, capable of holding?ve transport layer packets is well suited for Bluetooth devices(which typically have low memory resources) and also reduces the queueing delay.Assuming a transport layer packet of size512bytes,we concluded that even real time UDP applications running at32kb/s will not experience any packet drops.
We observed that a simple MAC scheduling algorithm such as Round-Robin is not suitable for Bluetooth as it is unable to minimize delay for interactive sessions.Further,it does not dis-tribute bandwidth fairly amongst all active sessions.With these issues in mind,we proposed and compared three new scheduling algorithms:AFP,Sticky and StickyAFP,which have a simple implementation.Our results highlight the signi?cant increase in performance obtained by their use.AFP and Sticky(with
thresh,in the ARQ scheme was found to be?ve.We demonstrated that the channel state depen-dent(CSDP)versions of the proposed scheduling algorithms do not lead to signi?cant gains in performance.Further,we showed that the presence of voice connections degrades the performance of data traf?c.We observed that the performance gains across TCP variants are marginal,from which we concluded that ef?-cient link-layer error recovery mechanisms in Bluetooth obviate the need for transport layer enhancements.
It is important to point out that the error model can be ex-tended,at the expense of an increased computational complex-ity,to a transmission channel modeled as a?nite state Markov chain with more than two states.Further study is required to incorporate low power modes(sniff,hold,park)into MAC scheduling and to explore the effect of varying number of slaves in a piconet.Since performance is expected to vary signi?cantly with varying channel status,a clever design of adaptive FEC and ARQ schemes may be very effective in Bluetooth.An important area of future research is to study the performance of TCP traf?c over a Bluetooth scatternet with multiple overlapping piconets. Many earlier papers have focussed on TCP performance over mobile ad-hoc networks(see[12]and the references therein),it however remains to be seen how TCP will perform over a Blue-tooth scatternet with a unique physical and TDD MAC layer.
A CKNOWLEDGMENT
The authors would like to thank Apurva Kumar(Research Staff Member,IBM India Research Laboratory,New Delhi,In-dia)and Vijay Gupta(Department of Electrical Engineering,In-dian Institute of Technology,New Delhi,India)for their help in designing the Bluetooth channel model.The parameters of the two state Markov model for Bluetooth have been obtained by them.
R EFERENCES
[1]Bluetooth Special Interest Group,“Speci?cation of the Bluetooth System
1.0b,V olume1:Core,”https://www.sodocs.net/doc/d36894292.html,,Dec.1999.
[2]J.Haartsen,“The Bluetooth Radio System,”IEEE Personal Communica-
tions,V ol.7,No.1,pp.28-36,Feb.2000.
[3]W.R.Stevens,TCP/IP Illustrated,Volume1:The Protocols,Addison Wes-
ley,1994.
[4]H.Chaskar and U.Madhow,“TCP over wireless with link level error con-
trol:Analysis and design methodology,”https://www.sodocs.net/doc/d36894292.html,COM,1996.
[5] A.Kumar,“Comparative performance analysis of versions of TCP in local
network with a lossy link,”IEEE/ACM Trans.on Networking,V ol.6,No.
4,pp.485-498,Aug.1998.
[6]H.Balakrishnan,V.N.Padmanabhan,S.Seshan and R.H.Katz,“A com-
parison of mechanisms for improving TCP performance over wireless links,”IEEE/ACM Trans.on Networking,V ol.5,No.6,pp.756-769,Dec.
1997.
[7]P.Bhagwat,P.Bhattacharya,A.Krishna and K.Tripathi,“Using channel
state dependent packet scheduling to improve TCP throughput over wire-less LANs,”Wireless Networks,pp.91-102,1997.
[8]K.Fall and S.Floyd,“Simulation-based Comparisons of Tahoe,Reno,and
Sack TCP,”ftp://https://www.sodocs.net/doc/d36894292.html,,Mar.1996.
[9]N.Johansson,M.Kihl and U.Korner,“TCP/IP over the Bluetooth wireless
ad-hoc network,”Networking2000,Paris,France,May2000.
[10]N.Johansson,U.Korner and P.Johansson,“Performance evaluation of
scheduling algorithms for Bluetooth”,In Broadband Communications: Convergence of Network Technologies,Edited by Danny H.K.Tsang and Paul J.Kuhn,Kluwer Academic Publishers,pp139-150,2000.
[11]M.Kalia,D.Bansal and R.Shorey,“MAC scheduling and SAR poli-
cies for Bluetooth:A master driven TDD pico-cellular wireless system”, IEEE International Workshop on Mobile Multimedia Communications (MoMuc’99),San Diego,CA,USA,pp.384-388,Nov.1999.
[12]G.Holland and N.Vaidya,“Analysis of TCP performance over mobile
ad hoc networks”,Fifth Annual ACM/IEEE International Conference on Mobile Computing and Networking(MobiCom’99),Seattle,USA,August, 1999.
[13]W.Simpson,“The Point-to-Point Protocol(PPP),”RFC1661,July1994.
[14]P.Bhagwat,I.Korpeoglu,C.Bisdikian,M.Naghshineh and S.K.Tripathi,
“Bluesky:A cordless networking solution for palmtop computers,”Mobi-com’99,Seattle,Washington,Aug.1999.
[15]S.McCanne and S.Floyd,“NS-Network Simulator,”1995,http://www-
https://www.sodocs.net/doc/d36894292.html,/ns.
[16] D.Moldkar,“Review on radio propagation into and within buildings,”IEE
Proc.-H,V ol.138,No.1,Feb.1991.
[17] D.Duchamp and N.Reynolds,“Measured performance of a wireless
LAN,”17th Conference on Local Computer Networks,Minneapolis,MN, pp.494-499,Sept.1992
[18]H.S.Wang and N.Moayeri,“Finite-state Markov channel-a useful model
for radio communication channels,”IEEE Trans.Veh.Technol.,V ol.44, pp.163-171,Feb.1995.
[19]G.T.Nguyen,B.D.Noble,R.H.Katz and M.Satyanarayanan,“A trace-
based approach for modeling wireless channel behavior,”in Proc.Winter Simulation Conf.,Dec.1996.
[20]M.Shimizu et al.,“New method of analyzing BER performance of GFSK
with postdetection?ltering,”IEEE https://www.sodocs.net/doc/d36894292.html,mun.,V ol.45,No.4,pp.
429-436,April1997.
[21]R.Ganesh and V.Pahlavan,“Effects of local traf?c and local movements
on the multipath characteristics of the indoor radio channel,”IEE Elect.
Let.,26(12),pp.810-812,1990.
(完整版)北师大版小学六年级数学毕业考试题及答案
小学六年级数学毕业测试题 一、填空。(28分。) 1、据统计,我国汉族人口是十一亿三千七百三十九万人,写作( ),省略“亿”后面的尾数约是( )人。 2、 5时24分=( )时 8050平方米=( )公顷 3456立方厘米=( )升 3千克50克=( )千克 3、填上合适的单位名称: 一个水桶高约4( ) 数学书的封面面积约为360( ) 一袋大米约重25( ) 喝水杯的的容积250( ) 4、( )/10=( ):45=6÷( )=2/5 5、一个三角形三个内角的度数比是5:3:1,这个三角形最大的角是( )度,这个三角形是( )三角形 6、一台收音机原价100元,先提价10%,又降价10%,现在售价是( )元。 7、经过两点可以画出( )条直线,两条直线相交有( )个交点。 8、找规律: (1)4、 9、16、( )、36、49。 (2)1/2、2/4、( )4/8、( )。 9、把3米长的绳子平均分成5段,每段占全长的( ),是( )米。 10、等底等高的圆柱和圆锥体积之差是4.6立方分米,圆柱的体积是( )立方分米。 11、鸡兔同笼,共有30个头,88只脚。求笼中鸡( )只,兔有( )只。 12、在一个口袋里有2个红球和8个黄球,从中任意摸出1个球,摸出红球的可能性是( ),如果摸10000次,摸出红球的可能性是( )次。 二、选择。(10分。) 1、长方体体积一定,底面积和高( ) ①成正比例;②成反比例;③不成比例;④既可能成批比例,又可能成正比例。 2、下列图形中对称轴最多的是( ) ① 长方形; ② 正方形; ③ 三角形; ④ 圆。 3、一个长方形框架拉成平行四边形后,面积( )。 ①不变; ②减小; ③增大; ④既可能减小又可能增大。 4、一个长方形、一个正方形和一个圆的周长相等,那么面积最大的是( ) ① 长方形 ② 正方形 ③ 圆 5、要反映小红六年级数学成绩变化情况,应选择( ) ①条形统计图 ②折线统计图 ③扇形统计图 三、计算。(28分) 1、直接写出得数(8分) 24.06+0.4= ( 5165-)×30= =+5 3 73 12.5×32×2.5= 121÷6= 5-(9792+)= 5 4×25= 2.8×25+12×2.5= 2、脱式计算,能简算的要写出简算过程。(18分) 85.87-(5.87+2.9) 1.25×7×0.8 54.2-2/9+4.8- 19 7 125)731(35÷-? 1387131287÷+? 11 8 )26134156(?-? 3.求未知数x 6/7x +4.8=5 χ-3/5 χ= 6/5 0.8x+1.2x =25 四、操作题 (6分) 1、把三角形向右移动5格; 2、把三角形绕B 点逆时针旋转900 , 3、把三角形按2:1的比放大。 (3分) 2、在下图上完成下列问题。(3分) (1)科技馆在学校北偏东30°方向2000米处。请在图中标出科技馆的位置,并标出数据。 (2)南京路经过电影院,与上海路平行。请用直线标出南京路的位置。
Petrophysical Evaluation for Enhancing Hydraulic Stimulation in Horizontal Shale Gas Wells
SPE 132990 Petrophysical Evaluation for Enhancing Hydraulic Stimulation in Horizontal Shale Gas Wells Dan Buller, Simon Hughes, Jennifer Market, and Erik Petre, Halliburton, and David Spain and Tobi Odumosu, BP America Copyright 2010, Society of Petroleum Engineers This paper was prepared for presentation at the SPE Annual Technical Conference and Exhibition held in Florence, Italy, 19–22 September 2010. This paper was selected for presentation by an SPE program committee following review of information contained in an abstract submitted by the author(s). Contents of the paper have not been reviewed by the Society of Petroleum Engineers and are subject to correction by the author(s). The material does not necessarily reflect any position of the Society of Petroleum Engineers, its officers, or members. Electronic reproduction, distribution, or storage of any part of this paper without the written consent of the Society of Petroleum Engineers is prohibited. Permission to reproduce in print is restricted to an abstract of not more than 300 words; illustrations may not be copied. The abstract must contain conspicuous acknowledgment of SPE copyright. Abstract The economic recovery of gas from shale reservoirs requires optimal multistage hydraulic stimulation in horizontal wells. Important parameters to consider in shale-gas evaluation include gas-filled porosity and total organic content. Mechanical rock properties, including a calculated brittleness index, along with mineralogy, are also required to target and design individual horizontal fracture stages in the best zones. This type of formation evaluation in horizontal wells requires careful correlation and calibration to petrophysical measurements obtained in either vertical pilot holes or direct offset wells. This paper presents a comprehensive approach to the evaluation of an unconventional resource play drilled in the Haynesville Shale in east Texas. Using openhole and logging-while-drilling (LWD) logs, conventional core analysis, and a chemostratigraphy analysis of drill cuttings, a shale analysis linking mineralogy, free gas, effective porosity, a shale brittleness index, and a clay linked transverse anisotropy is verified on separate vertical and horizontal control wells. Beyond that, pulsed neutron spectroscopy logs were run to develop a cased-hole evaluation solution from N-N (neural network) modeling that could replicate openhole wireline or LWD logs, and chemostratigraphy mineralogy results. Subsequently, two horizontal wells were logged with LWD tools and afterward, through casing, using the pulsed neutron log and neural network calibration. Fracture stages for the logged horizontal wells were then evaluated vs. the log data. Generally, lower normalized treating pressures per fracture stage are noted where lower clay volumes exhibit less transverse anisotropy and a higher calculated shale brittleness index. Radioactive tracer and production log data also confirm lower amounts of gas production from zones that are apparently fractured, but are more ductile and clay-rich. Introduction The Haynesville Shale is a black, organic-rich, shale that covers Caddo, Bossier, De Soto, Red River, and Bienville parishes in north Louisiana and primarily Harrison, Panola, Shelby, and San Augustine counties in east Texas The depth ranges from approximately 10,300 ft in the northwest part of the play to approximately 14,000 ft in the southeast. The Bossier Shale lies above the Haynesville Shale; the Haynesville Lime or Smackover Lime lie below it throughout the area. Both of these formations can be drilling targets, but the Haynesville Shale is of special interest because of generally thicker net pay and higher reservoir pressure with a gradient between 0.85 and 0.9 psi/ft. Varying depositional environments have left the shale with a thickness that varies between 80 and 350 ft, and facies that varies between a calcite-rich shale with little clay to a silica-rich shale with large amounts of bedded clay and lesser amounts of calcite (Parker et al. 2009). Advanced evaluation suites can provide an abundance of reservoir information. The primary purpose is resource identification and a calculation of original gas in place. However, new formation analysis and presentation techniques are required for a comprehensive mechanical description of this shale to select an optimum horizontal target (Rickman et al. 2008; Mullen et al. 2007). Subsequently, the same type of information can be used to select and design optimum fracture stages along the horizontal well. Currently, a few operators are beginning to log their horizontal wells, but are not using any log data to strategically locate or plan the horizontal fractures. The current completion practice is still evolutionary because more fracture stages per lateral have achieved better results as more surface area is contacted. Perforation clusters and spacing per fracture stage have been increased or decreased, depending on whether at the location or on the operator. The one constant is that fracture treating pressures and rates, depending on job design, all indicate serious stratigraphic formation differences that must be accounted for. Post-fracture
北师大版小学数学六年级知识点
北师大版小学数学六年级(上册)知识点 第一单元圆 1、使学生认识圆的特征:圆的半径、直径、圆心。认识在同圆内半径和直径的关系。知道圆是轴对称图形,有无数条对称轴,而这些对称轴都过圆心。知道生活中有了圆才使我们的生活更美好。 2、认识同心圆、等圆。知道圆的位置由圆心决定,圆的大小由半径或直径决定。等圆的半径相等,位置不同;而同心圆的半径不同,位置相同。 3、使学生知道圆的周长和圆周率的含义,掌握圆的周长的计算公式,能够正确地计算圆的周长.介绍祖冲之在圆周率研究上的成就,渗透爱国主义教育。在运用上,要能根据圆的周长算直径或半径,会算半圆的周长:圆的周长×1/2+直径。会求组合图形的周长。 4、了解圆的面积的含义,经历圆面积计算公式的推导过程,掌握圆面积计算公式。 5、能正确运用圆的面积公式计算圆的面积,并能运用圆面积知识解决一些简单实际的问题。会灵活运用圆的面积公式。已知圆的周长会算圆的面积,会求组合图形的面积。会算圆环的面积,并且知道在周长相等的情况下,正方形、长方形、圆三种图形中,圆的面积最大。 6、在估一估和探究圆面积公式的活动中,体会“化曲为直”的思想,初步感受极限思想。 第二单元百分数的应用 本单元重点讲解百分数在生活中的应用,知识点为: 1、知道百分数的意义:表示一个数是另一个数的百分之几的数,叫做百分数。百分数也叫做百分率或百分比。百分数通常不写成分数形式,而用百分号“%”
表示;百分数有时也定义为分母是100的分数,但百分数与分数是有区别的:分数既可表示具体的量,又可表示两个数量间的倍比关系;然而百分数只能表示两个数量间的倍比关系;所以是不名数,也就是不能带单位的数。 2、在具体情景中理解“增加百分之几”或“减少百分之几”的意义,加深对百分数意义的理解。 3、能解决有关“增加百分之几”或“减少百分之几”的实际问题,提高运用数学解决实际问题的能力,体会百分数与现实生活的密切联系。 4、知道出勤率、出粉率、成活率等百分数的意义及在实际生活中的应用,会计算这种百分数。 5、知道成数、打折的含义。表示一个数是另一个数十分之几、百分之几的数,叫做成数。打折就是按原价的百分之几十、十分之几出售。八五折就是按原价的85%出售。成数和折扣数不能用小数表示。 6、能解决“比一个数增加百分之几的数是多少”或“比一个数减少百分之几的数是多少”的实际问题。 7、进一步加强对百分数的意义的理解,并能根据百分数的意义列方程解决实际问题,会解含有百分数的方程。 8、能利用百分数的有关知识,解决一些与储蓄有关的实际问题,提高解决实际问题的能力。知道利息是本金存入银行过一段时间取出后多出来的钱;本金是存入银行的钱;利率就是某段时间中利息占本金的百分比;利息税是国家银行规定的针对利息收入的税收。会计算利息。利息=本金×利率×时间 9、结合储蓄等活动,学习合理理财,逐步养成不乱花钱的好习惯。 第三单元图形的变换 1、通过观察、操作、想象,知道一个简单图形是怎样经过平移或旋转制作复杂图形的过程,体验图形的变换,发展空间观念。并能借助方格纸上的操作和分析,有条理地表达图形的平移或旋转的变换过程。
Betaine and DMSO- Enhancing Agents for PCR
Figure 2. Amplification of a fragment of the human retinoblastoma gene with additives DMSO and
Figure 4. NMR analyses of betaine and two commercial PCR additives. Panel A
and specificity of PCR amplifications, their effects on the melting temperature of DNA may alter the optimal annealing conditions for a particular reaction. Therefore, it may be necessary to empirically determine the optimal annealing temperature if adding one or both of these agents to a particular amplification reaction. R EFERENCES 1.Sarkar, G., Kapelner, S. and Sommer, S.S. (1990) Nucl. Acids Res. 18, 7465. 2. Varadaraj, K. and Skinner, D.M. (1994) Gene 140, 1. 3.Baskaran, N. et al. (1996) Genome Res. 6, 633. 4.Weissensteiner, T. and Lanchbury, J.S. (1996) BioTechniques 21, 1102. 5. Hengen, P.N. (1997) Trends Bioch. Sci. 22, 225. 6.Henke, W. et al. (1997) Nucl. Acids Res. 25, 3957. 7.Melchior, W.B., Jr., and von Hippel, P.H. (1973) Proc. Natl. Acad. Sci. USA 70, 298. 8.Rees, W.A. et al. (1993) Biochemistry 32, 137. 9. Bookstein, R. et al. (1990) Nucl. Acids Res. 18, 1666. 10. PCR Handbook for Taq DNA polymerase and Taq PCR Core Kit (1996) Qiagen. 11.Advantage-GC TM cDNA PCR User Manual P3091-1 (1997) CLONTECH. ? 1998 Promega Corporation. All Rights Reserved. Advantage-GC is a trademark of CLONTECH Laboratories, Inc. Aldrich is a registered trademark of Aldrich Chemical Co. Perkin-Elmer is a registered trademark of The Perkin-Elmer Corporation. Triton is a registered trademark of Union Carbide Chemicals and Plastics Co., Inc. pGEM is a trademark of Promega Corporation and is registered with the U.S. Patent and Trademark Office. Product claims are subject to change. Please contact Promega Technical Services or access the Promega online catalog for the most up-to-date information on Promega products. Related Products Product Size Cat.#PCR Core System I 200 reactions M7660PCR Core System II 200 reactions M7665
Enhancing production of bio-isoprene using hybrid MVA pathway and isoprene synthase in E.coli
Enhancing Production of Bio-Isoprene Using Hybrid MVA Pathway and Isoprene Synthase in E.coli Jianming Yang1,Mo Xian1*,Sizheng Su2,Guang Zhao1,Qingjuan Nie3,Xinglin Jiang1,Yanning Zheng1, Wei Liu1 1Biomaterials Center,Qingdao Institute of Bioenergy and Bioprocess Technology,Chinese Academy of Sciences,Qingdao,China,2Department of Biochemistry,Beijing Risun Chemical Technologies Institute,China Risun Coal Chemicals Group Limited,Beijing,China,3College English Office,Foreign Languages School,Qingdao Agricultural University,Qingdao,China Abstract The depleting petroleum reserve,increasingly severe energy crisis,and global climate change are reigniting enthusiasm for seeking sustainable technologies to replace petroleum as a source of fuel and chemicals.In this paper,the efficiency of the MVA pathway on isoprene production has been improved as follows:firstly,in order to increase MVA production,the source of the‘‘upper pathway’’which contains HMG-CoA synthase,acetyl-CoA acetyltransferase and HMG-CoA reductase to covert acetyl-CoA into MVA has been changed from Saccharomyces cerevisiae to Enterococcus faecalis;secondly,to further enhance the production of MVA and isoprene,a alanine110of the mvaS gene has been mutated to a glycine.The final genetic strain YJM25containing the optimized MVA pathway and isoprene synthase from Populus alba can accumulate isoprene up to 6.3g/L after40h of fed-batch cultivation. Citation:Yang J,Xian M,Su S,Zhao G,Nie Q,et al.(2012)Enhancing Production of Bio-Isoprene Using Hybrid MVA Pathway and Isoprene Synthase in E.coli.PLoS ONE7(4):e33509.doi:10.1371/journal.pone.0033509 Editor:Spencer J.Williams,University of Melbourne,Australia Received December5,2011;Accepted February15,2012;Published April27,2012 Copyright:?2012Yang et al.This is an open-access article distributed under the terms of the Creative Commons Attribution License,which permits unrestricted use,distribution,and reproduction in any medium,provided the original author and source are credited. Funding:No funding has supported the work. Competing Interests:Sizheng Su is currently employed by China Risun Coal Chemicals Group Limited.There are no other relevant declarations relating to employment,consultancy,patents,products in development or marketed products for Sizheng Su or any other authors.This does not alter the authors’adherence to all the PLoS ONE policies on sharing data and materials. *E-mail:xianmo@https://www.sodocs.net/doc/d36894292.html, Introduction Isoprene(2-methyl-1,3-butadiene)was firstly discovered as a cell metabolite in the mid-1950s by Sanadze.[1,2].It functions as a thermoprotectant of plant membranes or as an antioxidant[3,4], or may have a signaling function,altering the flowering time in some plants[5].As an important platform chemical,isoprene has been used in industrial production of synthetic rubber for tires and coatings[6]or aviation fuel[7]. Isoprene is the progenitor of the isoprenoid family of compounds[8].Many commercially relevant isoprenoids exist in nature in small quantity and the yield produced from their natural organisms remains rather low.The depletion of fossil sources and the structural complexity of isoprenoids make it difficult or costly to produce isoprenoids by means of chemical synthesis.Isoprene is no exception since it is produced entirely from petrochemical sources through chemical synthesis method[9,10,11]. Compared with conventional means,microbial synthesis of isoprene by fermentation should become a promising and attractive route mainly for environmental production,renewable resources,sustainable development[12].Additionally,isoprene could be collected from the gas phase of the fermentor,eliminating the need for distillation.All isoprenoids are biosynthesized from the same basic units,isopentenyl diphosphate(pyrophosphate; IPP),and its isomer dimethylallyl diphosphate(DMAPP),which are synthesized from two different pathways including methyler-ythritol4-phosphate(MEP)pathway and mevalonate(MVA) pathway(Fig.1)[13].MVA pathway mainly exists in eukaryotes,archaebacteria,and cytosols of higher plants,while the MEP pathway is used by many eubacteria,green algae,and chloroplasts of higher plant[14,15].MVA pathway has been studied extensively for producing isoprenoids.The introduction of heterologous MVA pathway genes into E.coli has been reported to improve the productivity of carotenoids or sesquiterpenes that are synthesized from DMAPP[16,17,18,19,20,21,22]. Although MVA pathway has been studied comprehensively,the methylerythritol phosphate(MEP)pathway was merely discovered in the early1990s by labeling experiments in bacteria and plants[23,24],and till2001the genes of whole MEP pathway has been completely characterized[25].This biosynthetic pathway, made up of seven enzymatic steps,begins with the condensation of pyruvate and glyceraldehyde-3-phosphate to form1-deoxy-D-xylulose5-phosphate(DXP)and ends with the formation of the isoprenoid precursors isopentenyl diphosphate(IPP)and dimethy-lallyl diphosphate(DMAPP)[26,27].In spite of great efforts taken in isoprenoids production using MEP pathway[28,29,30],this approach still remains ineffective due to regulation mechanisms present in the native host[18]. In this paper,based on our previous experiments,the efficiency of the MVA pathway on isoprene production has largely been improved as follows:firstly,in order to increase MVA production, the source of the‘‘upper pathway’’which contains HMG-CoA synthase,acetyl-CoA acetyltransferase and HMG-CoA reductase to covert acetyl-CoA into MVA has been changed from Saccharomyces cerevisiae to Enterococcus faecalis;secondly,to further enhance the production of MVA and isoprene,a alanine110of
2018年北师大版小学六年级数学毕业试题共10套
六年级数学下册(北师大版)总复习综合练习题 班别:姓名:评分:等级: 一、填空题。(每空1分,共24分) 1、由3个十万,4个千组成的数写作(),改写成“万”为单位是 ()。 2、3时45分=()时 3.08升()毫升 3、1 2 千米:8米化成最简整数比是(),比值是()。 4、某地早晨气温-5℃,中午气温6℃,从早晨到中午气温上升了()℃。 5、60千克是40千克的()%,1米的3 5 和()米的20%一样长。 6、把4米长的铁丝平均截成8段,每段是这根铁丝的() () ,每段长()米。 7、36和48的最大公因数是(),最小公倍数是()。 8、在一张长是8分米,宽6分米的长方形卡纸中,剪一个面积最大的圆,这个圆的面积 是()平方分米。 9、一幅地图的比例尺是1:500000,表示实际距离是图上距离的()倍,在这幅地 图上量得甲、乙两地相距8.8厘米,甲、乙两地间的实际距离是()千米。 10、在24、22、20、26、26、26、这组数据中,中位数是(),众数是(), 平均数是()。 11、等底等高的圆柱与圆锥的体积总和是60立方米,那么圆柱的体积是()立方米, 圆锥的体积是()立方米。 12、4根小棒长分别是2厘米,3厘米、5厘米,7厘米,选其中的三根,围成一个三角形, 三角形的周长是()厘米。 13、摆一个三角形需要3根小棒,摆两个三角形需要5根,摆3个三角形需要() 根小棒,摆m个三角形需要()根小棒。 二、判断题(正确的在括号里打“√”,错的打“×”)。(5分) 1、0.8和0.80的大小相等,计数单位也一样。() 2、圆的面积和它的半径成正比例。() 3、师徒两人共同生产一批零件,徒弟生产的零件合格率是90%,那么师傅生产的零件合 格率是110%。()
Enhancing the Taste of Our Food
Enhancing the Taste of Our Food A What are your favorite foods? Do you like pizza, hamburgers, roast pork, or sweet cakes and cookies? Chances are that, whatever you like best, it has a strong taste and a salty, sweet or savory flavor. People generally like to eat tasty foods, and this can create potential health problems, especially with the consumption of fast or processed food. Fast food traditionally contain a lot of salt or sugar, because this is a cheap way to make food taste good and it encourages people to buy more cookies, chips and soft drinks, for example. However, people are becoming increasingly aware of the dangers of an unhealthy diet, and the manufacturers of processed food know that sales will increase if they can advertise that their products have less salt or sugar. They also know that if their product tastes bland or boring, no amount of health benefits will make it a popular choice with consumers, and they will lose money if their product is not popular. However, a new technology is currently being developed that may allow fast food manufacturers to reduce salt and sugar without sacrificing taste. B If you stick out your tongue and look in the mirror, you will see that it is covered with tiny bumps. These bumps are called taste buds and they are the receptors in your skin that allow us to taste different kinds of foods. There are five different taste receptors, for sweet, salty, sour, bitter and savory flavors. When we are born we have a lot of these on the roof of our mouth as well as on our tongue, but as we get older, we lose taste buds, which is why older people find it harder to taste things. Adults typically have about 10,000 taste buds, but older people may have as few as 5,000. We have more receptors for bitter tastes than for any others; researchers think that this may be because these taste buds warn us if food is poisonous. C The food that we eat contains natural chemicals that fit into the different shaped receptors on our tongues; for example, sweet foods trigger the sweet receptors. The technology to mimic, or copy, these natural flavors with chemicals such as aspartame is a common ingredient in many diet soft drinks and other diet products. While aspartame allows us to experience a sweet taste without eating sugar, it also has disadvantages. Firstly, many people do not like its bitter aftertaste, and secondly, some people say that it is bad for health if taken in large quantities. D However, a new technology is being developed that may be an improvement on artificial sweeteners and other chemicals. Taste enhancers target the taste receptors on our tongues and they make us more sensitive to sweet, sour or salty tastes. Just a few molecules of a taste enhancer could double the sweetness effect of a teaspoon of sugar, or the salty effect of a teaspoon of salt. This means that instead of using artificial chemicals to make food tasty, food manufacturers could use half the quantity of the real substance and a tiny quantity of taste enhancer to make the food taste good. This has the potential to save food manufacturers money, by replacing large quantities of sugar and salt with tiny amounts of chemicals. It could also benefit our health if we can eat food that tastes good and is low in sugar and salt.
相关文档
- Betaine and DMSO- Enhancing Agents for PCR
- Enhancing the Consumer-Product Relationship Lessons from the QVC Home Shopping Channel
- 兴奋剂 Performance Enhancing Drugs
- Petrophysical Evaluation for Enhancing Hydraulic Stimulation in Horizontal Shale Gas Wells
- Enhancing the development of speaking skills for non-native learners
- Enhancing the Taste of Our Food
- Enhancing Sparsity by Reweighted l1 Minimization
- 幼小衔接专家教授讲座PPT模板
- Enhancing production of bio-isoprene using hybrid MVA pathway and isoprene synthase in E.coli
- Enhancing-the-Taste-of-Our-Food
- 词义辨析
