An Efficient Identity-Based Conditional

An Ef?cient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks Debiao He,Sherali Zeadally,Baowen Xu,Member,IEEE,and Xinyi Huang
Abstract—By broadcasting messages about traf?c status to vehicles wirelessly,a vehicular ad hoc network(V ANET)can improve traf?c safety and ef?ciency.To guarantee secure com-munication in V ANETs,security and privacy issues must be addressed before their deployment.The conditional privacy-preserving authentication(CPPA)scheme is suitable for solving security and privacy-preserving problems in V ANETs,because it supports both mutual authentication and privacy protection simultaneously.Many identity-based CPPA schemes for V ANETs using bilinear pairings have been proposed over the last few years to enhance security or to improve performance.However,it is well known that the bilinear pairing operation is one of the most complex operations in modern cryptography.To achieve better performance and reduce computational complexity of information processing in V ANET,the design of a CPPA scheme for the V ANET environment that does not use bilinear paring becomes a challenge.To address this challenge,we propose a CPPA scheme for V ANETs that does not use bilinear paring and we demonstrate that it could supports both the mutual authentication and the privacy protection simultaneously.Our Manuscript received May14,2015;revised July24,2015;accepted July24,2015.Date of publication August31,2015;date of current version September30,2015.The work of D.He was supported in part by the National Natural Science Foundation of China under Grant61373169,Grant61572379, and Grant61501333,in part by the National High-Tech Research and Development Program of China(863Program)under Grant2015AA016004, in part by the Fujian Provincial Key Laboratory of Network Security and Cryp-tology Research Fund through Fujian Normal University under Grant15011, and in part by the Natural Science Foundation of Hubei Province of China under Grant2015CFB257.The work of B.Xu was supported in part by the National Natural Science Foundation of China under Grant91418202 and Grant61472178and in part by the National Key Basic Research and Development Program of China under Grant2014CB340702.The work of X.Huang was supported in part by the National Natural Science Foundation of China under Grant61472083and Grant U1405255,in part by the Fok Ying Tung Education Foundation under Grant141065,in part by the Program for New Century Excellent Talents in Fujian University under Grant JA14067, in part by the Distinguished Young Scholars Fund,Fujian Province,China, and in part by the State Key Laboratory of Cryptology Research Fund.The associate editor coordinating the review of this manuscript and approving it for publication was Prof.Willy Susilo.(Corresponding author:Xinyi Huang.)
D.He is with the State Key Laboratory of Software Engineering,Computer School,Wuhan University,Wuhan430072,China,and also with the Fujian Provincial Key Laboratory of Network Security and Cryptology,Fujian Normal University,Fuzhou350007,China(e-mail:hedebiao@https://www.sodocs.net/doc/3a4249400.html,). S.Zeadally is with the College of Communication and Information,Univer-sity of Kentucky,Lexington,KY40506USA(e-mail:szeadally@https://www.sodocs.net/doc/3a4249400.html,).
B.Xu is with the Department of Computer Science and Technology,Nanjing University,Nanjing210093,China(e-mail:bwxu@https://www.sodocs.net/doc/3a4249400.html,).
X.Huang is with the Fujian Provincial Key Laboratory of Network Security and Cryptology,School of Mathematics and Computer Science,Fujian Normal University,Fujian350007,China,and also with the State Key Laboratory of Cryptology,Beijing100878,China(e-mail:xyhuang81@https://www.sodocs.net/doc/3a4249400.html,).
Color versions of one or more of the?gures in this paper are available online at https://www.sodocs.net/doc/3a4249400.html,.
Digital Object Identi?er10.1109/TIFS.2015.2473820proposed CPPA scheme retains most of the bene?ts obtained with the previously proposed CPPA schemes.Moreover,the proposed CPPA scheme yields a better performance in terms of computation cost and communication cost making it be suitable for use by the V ANET safety-related applications.
Index Terms—Authentication,bilinear pairing,elliptic curve, vehicular ad-hoc networks.
I.I NTRODUCTION
T HE Vehicular Ad-hoc Network(V ANET),a variant of the Mobile Ad-hoc Network(MANET),is a continu-ously self-con?guring,infrastructure-less network which has emerged as a result of advances in wireless communications and networking technologies over the last few years[1]–[4]. Mobile nodes in V ANETs are vehicles equipped with On-Board Units(OBUs),which are wireless communication devices.OBUs enable vehicles in V ANETs to exchange traf?c messages with nearby mobile nodes.
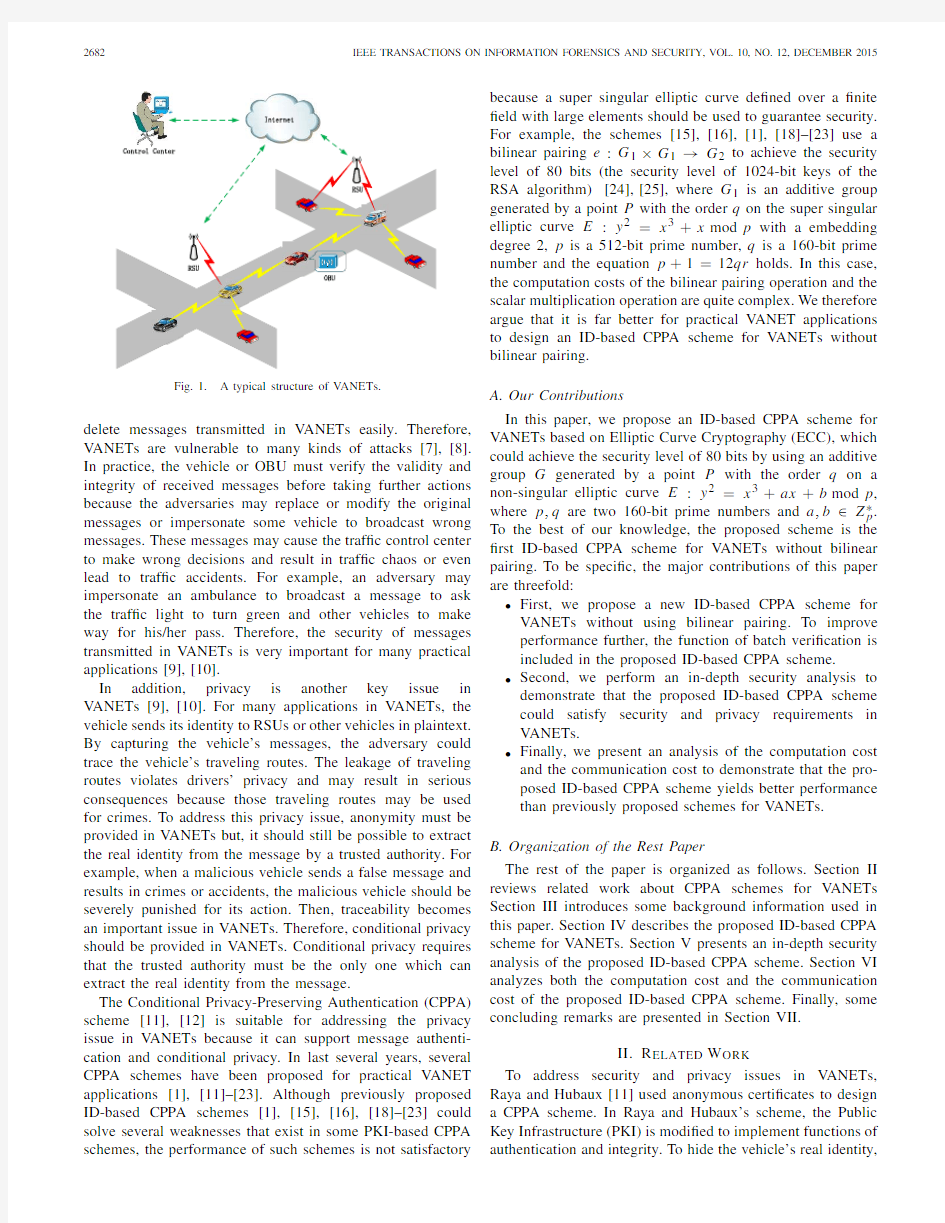
A typical structure of the V ANET is shown in Fig. 1. Communications in V ANETs can be divided into two types: Vehicle-to-Vehicle(V2V)communication and Vehicle-to-Infrastructure(V2I)communication.Both types of com-munications are controlled by a short-range wireless communication protocol,called the Dedicated Short Range Communication(DSRC)protocol.By using the OBU and the DSRC protocol,each vehicle can communicate with nearby vehicles and Road Side Units(RSUs)located at roadside and can communicate with the traf?c control center through the Internet.According to the speci?cation of the DSRC protocol, each vehicle periodically broadcasts messages about road traf?c and vehicles’conditions every100–300milliseconds, where road traf?c conditions include weather conditions,road defects,congestion situation,etc.and vehicle’s conditions include location,speed,traf?c status,etc.[5],[6].Upon receipt of these messages,other vehicles could change their traveling routes in order to avoid possible traf?c events such as traf?c congestion,traf?c accident,etc.Besides,RSUs can also send messages about traf?c conditions to the traf?c control center. Based on received messages,the traf?c control center can take some timely actions(such as adjusting traf?c lights)to improve traf?c safety and ef?ciency.All the aforementioned bene?ts make V ANET a promising technology for the modern intelligent transportation system.
Due to the wireless communication mode,adversaries against V ANETs could control communication channels fairly easily,i.e.adversaries could intercept,modify,replay and
1556-6013?2015IEEE.Personal use is permitted,but republication/redistribution requires IEEE permission.
See https://www.sodocs.net/doc/3a4249400.html,/publications_standards/publications/rights/index.html for more information.
Fig.1.A typical structure of V ANETs.
delete messages transmitted in V ANETs easily.Therefore, V ANETs are vulnerable to many kinds of attacks[7],[8]. In practice,the vehicle or OBU must verify the validity and integrity of received messages before taking further actions because the adversaries may replace or modify the original messages or impersonate some vehicle to broadcast wrong messages.These messages may cause the traf?c control center to make wrong decisions and result in traf?c chaos or even lead to traf?c accidents.For example,an adversary may impersonate an ambulance to broadcast a message to ask the traf?c light to turn green and other vehicles to make way for his/her pass.Therefore,the security of messages transmitted in V ANETs is very important for many practical applications[9],[10].
In addition,privacy is another key issue in V ANETs[9],[10].For many applications in V ANETs,the vehicle sends its identity to RSUs or other vehicles in plaintext. By capturing the vehicle’s messages,the adversary could trace the vehicle’s traveling routes.The leakage of traveling routes violates drivers’privacy and may result in serious consequences because those traveling routes may be used for crimes.To address this privacy issue,anonymity must be provided in V ANETs but,it should still be possible to extract the real identity from the message by a trusted authority.For example,when a malicious vehicle sends a false message and results in crimes or accidents,the malicious vehicle should be severely punished for its action.Then,traceability becomes an important issue in V ANETs.Therefore,conditional privacy should be provided in V ANETs.Conditional privacy requires that the trusted authority must be the only one which can extract the real identity from the message.
The Conditional Privacy-Preserving Authentication(CPPA) scheme[11],[12]is suitable for addressing the privacy issue in V ANETs because it can support message authenti-cation and conditional privacy.In last several years,several CPPA schemes have been proposed for practical V ANET applications[1],[11]–[23].Although previously proposed ID-based CPPA schemes[1],[15],[16],[18]–[23]could solve several weaknesses that exist in some PKI-based CPPA schemes,the performance of such schemes is not satisfactory because a super singular elliptic curve de?ned over a?nite ?eld with large elements should be used to guarantee security.
For example,the schemes[15],[16],[1],[18]–[23]use a bilinear pairing e:G1×G1→G2to achieve the security level of80bits(the security level of1024-bit keys of the
RSA algorithm)[24],[25],where G1is an additive group generated by a point P with the order q on the super singular elliptic curve E:y2=x3+x mod p with a embedding degree2,p is a512-bit prime number,q is a160-bit prime number and the equation p+1=12qr holds.In this case, the computation costs of the bilinear pairing operation and the scalar multiplication operation are quite complex.We therefore argue that it is far better for practical V ANET applications to design an ID-based CPPA scheme for V ANETs without bilinear pairing.
A.Our Contributions
In this paper,we propose an ID-based CPPA scheme for V ANETs based on Elliptic Curve Cryptography(ECC),which could achieve the security level of80bits by using an additive group G generated by a point P with the order q on a non-singular elliptic curve E:y2=x3+ax+b mod p, where p,q are two160-bit prime numbers and a,b∈Z?p. To the best of our knowledge,the proposed scheme is the ?rst ID-based CPPA scheme for V ANETs without bilinear pairing.To be speci?c,the major contributions of this paper are threefold:
?First,we propose a new ID-based CPPA scheme for V ANETs without using bilinear pairing.To improve performance further,the function of batch veri?cation is included in the proposed ID-based CPPA scheme.?Second,we perform an in-depth security analysis to demonstrate that the proposed ID-based CPPA scheme could satisfy security and privacy requirements in V ANETs.
?Finally,we present an analysis of the computation cost and the communication cost to demonstrate that the pro-posed ID-based CPPA scheme yields better performance than previously proposed schemes for V ANETs.
https://www.sodocs.net/doc/3a4249400.html,anization of the Rest Paper
The rest of the paper is organized as follows.Section II reviews related work about CPPA schemes for V ANETs Section III introduces some background information used in this paper.Section IV describes the proposed ID-based CPPA scheme for V ANETs.Section V presents an in-depth security analysis of the proposed ID-based CPPA scheme.Section VI analyzes both the computation cost and the communication cost of the proposed ID-based CPPA scheme.Finally,some concluding remarks are presented in Section VII.
II.R ELATED W ORK
To address security and privacy issues in V ANETs, Raya and Hubaux[11]used anonymous certi?cates to design a CPPA scheme.In Raya and Hubaux’s scheme,the Public Key Infrastructure(PKI)is modi?ed to implement functions of authentication and integrity.To hide the vehicle’s real identity,
HE et al.:EFFICIENT IDENTITY-BASED CPPA SCHEME FOR V ANETs2683
many public/private key pairs and corresponding certi?cates are pre-loaded into vehicles’OBUs.In each communication, the vehicle’s OBU chooses a pair of public/private key randomly and uses them to implement functions of authentica-tion and integrity.Raya and Hubaux’s scheme[9]suffers from the following weaknesses:1)Each vehicle should have very large storage space to store its public/private key pairs and the corresponding certi?cates;2)The authority should also have
a very large storage space to store all vehicles’certi?cates;
3)It is dif?cult to?nd the adversary’s real identity when he/she sends the wrong message because the authority has to perform an exhaustive search of all stored certi?cates.
To address the weaknesses in Raya and Hubaux’s scheme, Lu et al.[12]proposed a new CPPA scheme using anonymous certi?cates.The vehicle in Lu et al.’s CPPA scheme obtains a temporary anonymous certi?cate when it passes by a RSU. To achieve conditional privacy,each vehicle has to request a new anonymous certi?cate from a RSU frequently because the adversary could trace a vehicle if a certi?cate is used for a long time.However,frequent interactions with RSUs are not ef?cient.Therefore,Lu et al.’s CPPA scheme cannot satisfy the requirement of ef?ciency in V ANETs[13].To overcome the weakness in Lu et al.’s CPPA scheme,Freudiger et al.[13] combined technologies of anonymous certi?cates and mix-zones to design a new CPPA scheme.However,in this modi?ed CPPA scheme,the vehicles and the RSUs have to store a large number of anonymous certi?cates. Zhang et al.[14]used the Hash Message Authentication Code(HMAC)to construct an ef?cient CPPA scheme for V ANETs where the key for the HMAC is generated through a key agreement protocol executed between the vehicle and the RSU.To achieve privacy,the vehicle must use different private/public key pair along with the corresponding certi?cate in each communication with the RSU.Therefore, vehicles have to store a large number of private/public key pairs and the corresponding certi?cates.
To address the certi?cate management problem in the above PKI-based CPPA schemes[11]–[14],Zhang et al.[15],[16] incorporated the IDentity-based Public Key Cryptography (ID-based PKC)into the design of CPPA schemes.The concept of the ID-based PKC was proposed by Shamir[17] in1984.The identity(such as name,email and phone number) of the user in the ID-based PKC is his/her public key and his/her private key is generated by a trusted third party called the Private Key Generator(PKG).In this case,no certi?cate is needed to bind the user’s identity to his/her public key.Therefore,the ID-based PKC could solve the certi?cate management problem in the PKI.Zhang et al.[15],[16] proposed an Identity-Based Signature(IBS)scheme and used it in an Identity-based Conditional Privacy-Preserving Authentication(ID-based CPPA)scheme for V ANETs.Neither the vehicle nor the RSU in Zhang et al.’s ID-based CPPA scheme needs to store a certi?cate.Besides,their scheme incurs a lower veri?cation cost because it supports the function of batch veri?cation,i.e.,it could verify the validity of many messages simultaneously.Therefore,Zhang et al.’ID-based CPPA scheme could overcome weaknesses in previous PKI-based CPPA schemes[11]–[14].
However,as Lee and Lai[18]pointed out,Zhang et al.’ID-based CPPA scheme[15],[16]is vulnerable to the replay attack and cannot satisfy the property of non-repudiation. Later,Chim[1]pointed Zhang et al.’s ID-based CPPA scheme is vulnerable to the impersonation attack and the anti-traceability attack.Chim[1]also proposed another ID-based CPPA scheme for V ANETs.With only two shared secrets, Chim’s ID-based CPPA scheme[1]could satisfy the privacy requirements in V ANETs.Besides,Chim’s ID-based CPPA scheme[1]has lower communication costs than previously proposed ID-based CPPA schemes.However,Horng et al.[19] found that Chim’s ID-based CPPA scheme was vulnerable to the impersonation attack,i.e.,a malicious vehicle could imper-sonate any another vehicle to broadcast counterfeit messages. To improve performance,Shim[20]proposed an ef?cient IBS scheme and used it to design an ef?cient ID-based CPPA schemes.Unfortunately,Liu et al.[21]pointed out that a security?aw exists in the proof of Shim’s IBS scheme and Shim’s ID-based CPPA scheme suffers from a modi?cation attack,i.e.,the adversary can generate a new legal message by modifying a previous message.
Recently,Zhang et al.[22]and Bayat et al.[23]found that Lee and Lai’s ID-based CPPA scheme[18]cannot withstand the impersonation attack,i.e.,a malicious vehicle could impersonate any other vehicle to broadcast a forged message.Zhang et al.[22]also pointed out that Lee and Lai’s ID-based CPPA scheme[18]cannot provide non-repudiation of messages.To enhance the security of previous schemes, Zhang et al.[22]and Bayat et al.[23]also proposed two improved ID-based CPPA schemes for V ANETs. By modifying the process of generating the anonymous identity and the digital signature,Zhang et al.’s ID-based CPPA scheme[22]and Bayat et al.’s ID-based CPPA scheme[23]could solve security problems in Lee and Lai’s ID-based CPPA scheme[18]and have better computation performance results.Despite these improvements, Zhang et al.ID-based CPPA scheme[22]and Bayat et al.’s ID-based CPPA scheme[23]still suffer from the modi?cation attack proposed by Liu et al.[21].
III.B ACKGROUND
https://www.sodocs.net/doc/3a4249400.html,work Model
According to novel research[26]–[28],the two-layer network model is very suitable for V ANETs.The various components of the network model are shown in Fig.2.
The upper layer of the network model consists of a Trusted Authority(TA)and an Application Server(AS),where they could communicate with each other through a secure channel that can be established through the Secure Socket Layer(SSL) protocol.The bottom layer of the network model consists of a RSU and a vehicle,where they could communicate with each other through the DSRC protocol.The details of those four participants are described as follows.
?TA:The TA is a trusted third party with high computation and communication capabilities.It is responsible for generating system parameters and preloading them in the OBU of the vehicle of?ine.It is the only participant
2684IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY,VOL.10,NO.12,DECEMBER
2015
Fig.2.The network model for V ANET.
that could get the real identity of the vehicle from the intercepted messages.
?
AS :The AS could support safety-related applications at the traf?c management center.The AS could communi-cate with RSUs for providing application support.
?
RSU :The RSU is a wireless communication device that uses the DSRC protocol.It is located at roadside and could communicate with vehicles.It can verify the validity of received messages and sends them to the traf?c management center or process them locally.
?
Vehicle :The vehicle is equipped an OBU supporting the DSRC protocol.The OBU is a tamper-proof device and its information is never disclosed.The vehicle communi-cates wirelessly with RSUs using the OBU.
B.Security and Privacy Requirements
Both security and privacy are important for secure com-munications in V ANETs.Based on the latest research efforts [1],[17]–[23],[26]–[28],an ID-based CPPA scheme for V ANETs should meet the following security require-ments:message authentication,identity privacy preservation,traceability,un-linkability and resistance to attacks,where the de?nition of the conditional privacy is expressed by the com-bination of the identity privacy preservation and traceability.1)Message authentication :RSUs are able to check the validity of the messages sent by vehicles.In addition,RSUs are able to detect any modi?cation of the received message.
2)Identity privacy preservation :RSUs and other vehicles are not able to extract the vehicle’s real identity.Any third party is not able to get the vehicle’s real identity by analyzing intercepted messages.
3)Traceability :The TA is able to extract the vehicle’s real identity by analyzing its messages when it is necessary.For example,a malicious vehicle sends a false message to mislead others.
4)Un-linkability :RSUs and malicious vehicles are not able to link two messages sent by the same vehicle,i.e.,they cannot trace the vehicle’s action through its messages.
5)Resistance to attacks :The ID-based CPPA scheme is able to withstand various common attacks such as the imper-sonation attack,the modi?cation attack,the replay attack,
the man-in-the-middle attack,and the stolen veri?er table attack that exist in V ANETs.
IV.T HE P ROPOSED ID-B ASED CPPA S CHEME
In this section,we propose our ID-based CPPA scheme without the bilinear pairing for V ANETs based on Schnorr’s signature scheme [29].The proposed CPPA scheme could be used for both V2I and V2V communications.There are three phases in the proposed ID-based CPPA scheme:the system initialization phase,the anonymous identity generation and message signing phase and the message veri?cation phase.We de?ne the notations used below as follows:?p ,q :two large prime numbers.
?E :an elliptic curve de?ned by the equation y 2=x 3+ax +b mod p ,where a ,b ∈F p .
?G :an additive group with the order q ,where G consists of all points on the elliptic curve E and the point at in?nity O .
?P :a generator of the group G .
?Discrete Logarithm (DL)problem:Given two random points P and Q on E ,the task of the DL problem is computing an integer x to satisfy the equation Q =x P .?Computational Dif?e-Hellman (CDH)problem:Given two random points Q and R on E ,the task of the CDH problem is computing the point x y P ,where Q =x P ,R =y P and x ,y are two unknown integers.?x :the private key of the system.
?P pub :the public key of the system,where P pub =x ·P .?RI D :the real identity of a vehicle.
?PW D :the password of the tamper-proof device.?AI D :the anonymous identity of a vehicle.
?h 1,h 2,h 3:three secure functions,where h 1:G →Z q ,h 2:{0,1}?→Z q and h 3:{0,1}?×{0,1}?×G ×{0,1}?→Z q .
?⊕:the exclusive-OR operation.
?||:the message concatenation operation.A.System Initialization Phase
In this phase,the TA generates system parameters (such as a ?nite ?led and an elliptic curve de?ned on it).The TA pre-loads them into each vehicle’s tamper-proof device and sends them to all RSUs.The following steps are executed by the TA in this phase.
1)The TA chooses two large prime numbers p ,q and a non-singular elliptic curve E de?ned by the equation y 2=x 3+ax +b mod p ,where a ,b ∈F p .
2)The TA chooses a generator P with order q of the group G ,which consists of all points on the elliptic curve E and the point at in?nity O .
3)The TA chooses a random number x ∈Z ?q
as the private key of the system and computes the system public key P pub =x ·P .
4)The TA chooses three secure hash functions h 1,h 2,h 3,where h 1:G →Z q ,h 2:{0,1}?→Z q and h 3:{0,1}?×{0,1}?×G ×{0,1}?→Z q .
5)The TA assigns a real identity RI D and a password PW D for each vehicle and pre-loads {RI D ,PW D ,x }into its tamper-proof device.
HE et al.:EFFICIENT IDENTITY-BASED CPPA SCHEME FOR V ANETs2685
6)The TA sends the system parameters parmas= {p,q,a,b,P,P pub,h1,h2,h3}to all RSUs and vehicles. B.Anonymous Identity Generation and
Message Signing Phase
In this phase,the vehicle’s tamper-proof device generates an anonymous identity and a digital signature of a message. After that,the vehicle broadcasts the anonymous identities,the message and the digital signature to nearby RSUs and vehicles. The following steps are executed during this phase.
1)The vehicle inputs its real identity RI D and password PW D into its tamper-proof device.The tamper-proof device checks if RI D and PW D are equal to the stored ones.The tamper-proof device rejects the request if one of them and the corresponding stored one are not equal.
2)The tamper-proof device generates a random number w i∈Z?q and computes AI D i,1=w i·P,AI D i,2= RI D⊕h1(w i·P pub),αi=h2(AI D i||T i),and sk i=w i+αi·x mod q,where AI D i={AI D i,1,AI D i,2}and T i is the current timestamp.Then,the tamper-proof device gives {AI D i,sk i,T i}to the vehicle.
3)The vehicle generates a random number r i∈Z?q,and computes R i=r i·P,βi=h3(AI D i||T i||R i||M i)and σi=sk i+βi·r i mod q,where M i is a message about traf?c status.Then,the vehicle broadcasts{M i,AI D i,T i,R i,σi}to nearby RSUs and vehicles.
C.Message Veri?cation Phase
In this phase,the veri?er(a RSU or a vehicle)checks the validity of received messages.The veri?er could check the validity of a received message through the traditional veri?ca-tion process.To improve performance,the proposed ID-based CPPA scheme supports the batch veri?cation function which enables the veri?er to check the validity of lots of messages simultaneously.The single veri?cation of one message and the batch veri?cation of multiple messages are described as follows.
?Single veri?cation of one message:Upon receiving a message{M i,AI D i,T i,R i,σi}sent by a vehicle,the veri?er uses the system parameters parmas={p,q,a,b,P,P pub, h1,h2,h3}to verify the validity of the message through the following steps.
1)The veri?er checks the freshness of T i.If it is not fresh, the veri?er rejects the message.
2)The veri?er checks whether the equationσi·P= AI D i,1+αi·P pub+βi·R i holds.If it does not hold,the veri?er rejects the message;otherwise,the veri?er accepts the message.
Due to P pub=x·P,AI D i,1=w i·P,AI D i,2=RI D⊕h1(w i·P pub),αi=h2(AI D i||T i),sk i=w i+αi·x mod q, R i=r i·P,βi=h3(AI D i||T i||R i||M i)andσi=sk i+βi·r i mod q,we could get that
σi·P=(sk i+βi·r i)·P
=(w i+αi·x+βi·r i)·P
=w i·P+αi·x·P+βi·r i·P
=AI D i,1+αi·P pub+βi·R i(1)
Therefore,the correctness of the single veri?cation of one message is proved.
?Batch veri?cation of multiple messages:To guarantee the non-repudiation of signatures using batch veri?cation,we use the small exponent test technology[19],[22]in the batch veri?cation of multiple messages.A vector,consisting of small random integers,is used to quickly detect any modi?cation of a batch of signatures in the small exponent test technology. Upon receiving multiple messages{M1,AI D1,T1,R1,σ1}, {M2,AI D2,T2,R2,σ2},…,{M n,AI D n,T n,R n,σn}sent by some vehicles,the veri?er uses the system parameters parmas={p,q,a,b,P,P pub,h1,h2,h3}to verify the valid-ity of those messages through the following steps.
1)The veri?er checks the freshness of T i,where i=1,2,...,n.If it is not fresh,the veri?er rejects the message.
2)The veri?er chooses a vector v={v1,v2,...,v n} randomly,where v i is a small random integer in[1,2t]and t is a small integer and has very little computation overhead. Afterwards,the veri?er checks if the following equation holds.
n
i=1
v i·σi
·P=
n
i=1
v i·AI D i,1
+
n
i=1
(v i·αi)
·P pub
+
n
i=1
(v i·βi·R i)(2)
If it does not hold,the veri?er rejects the messages;otherwise, the veri?er accepts the messages.
Due to P pub=x·P,AI D i,1=w i·P,AI D i,2=RI D⊕h1(w i·P pub),αi=h2(AI D i||T i),sk i=w i+αi·x mod q, R i=r i·P,βi=h3(AI D i||T i||R i||M i)andσi=sk i+βi·r i mod q,we could get that
n
i=1
v i·σi
·P=
n
i=1
v i·(sk i+βi·r i)
·P
=
n
i=1
v i·(w i+αi·x+βi·r i)
·P
=
n
i=1
(v i·(w i·P+αi·x·P+βi·r i·P))
=
n
i=1
v i·AI D i,1+v i·αi·P pub
+v i·βi·R i
=
n
i=1
v i·AI D i,1
+
n
i=1
v i·αi·P pub
+
n
i=1
(v i·βi·R i)
=
n
i=1
v i·AI D i,1
+
n
i=1
(v i·αi)
·P pub
+
n
i=1
(v i·βi·R i)(3)
Therefore,the correctness of the batch veri?cation of multiple messages is proved.
2686IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY,VOL.10,NO.12,DECEMBER 2015
V.S ECURITY A NALYSIS AND C OMPARISONS
In this section,we analyze the security of the proposed ID-based CPPA scheme for V ANETs.We demonstrate that it is able to meet all security and privacy requirements described in Section 2.First of all,we show that the proposed scheme is able to enforce non-forgery.We also compare the security of the proposed ID-based CPPA scheme for V ANETs with three most recently proposed CPPA schemes.A.Security Analysis
Based on the network model and the adversaries’ability,the security model for the CPPA scheme is de?ned through a game played between a challenger C and an adversary A .The adversary A could make the following queries in the game.?Setup ?Oracle :In this query,C generates the private key of the system and the system parameters.C sends the system parameters to A .
?h 1?Oracle :In this query,C chooses a random number r ∈Z q ,inserts the tuple (m ,r )into the list L h 1and returns r to A .
?h 2?Oracle :In this query,C chooses a random point r ∈Z q ,inserts the tuple (m ,r )into the list L h 2and returns r to A .
?h 3?Oracle :In this query,C chooses a random point r ∈Z q ,inserts the tuple (m ,r )into the list L h 3and returns r to A .
?Sign ?Oracle :In this query,C generates a request message {M i ,AI D i ,T i ,R i ,σi }upon receiving the mes-sage M i about traf?c status.C sends {M i ,AI D i ,T i ,R i ,σi }to A .
The adversary A could violate the authentication of the CPPA scheme if it could generate a login request message.
Let Adv Auth
(A )denote the probability that A could violate the authentication of the CPPA scheme .
De?nition 1:A CPPA scheme for V ANETs is secure if Adv Auth
(A )is negligible for any polynomial adversary A .We have evaluated the security of the proposed ID-based CPPA scheme for V ANETs and demonstrated that the pro-posed scheme is secure in the random oracle.
Theorem 1:The proposed ID-based CPPA scheme for V ANETs is secure in the random oracle model.
Proof:Suppose there is an adversary A that can forge a message {M i ,AI D 1,T i ,R i ,σi }.We can construct a chal-lenger C ,which could solve the DL problem with a non-negligible probability by running A as a subroutine.Given an instance (P ,Q =x ·P )of the DL problem,C simulates oracles queried by A as follows.
Setup ?Oracle :C sets P pub ←Q ,and sends the system parameters parmas ={p ,q ,a ,b ,P ,P pub ,h 1,h 2,h 3}to A .h 1?Oracle :C keeps a list L h 1with the form of ,τ ,which is initialized to empty.Upon receiving A ’s query with the message ,C checks whether a tuple ,τ exists in L h 1?rst.If so,C sends τ=h 1( )to A ;otherwise,C generates a random number τ∈Z q ,adds ,τ in L h 1and sends τ=h 1( )to A .
h 2?Oracle :C keeps a list L h 2with the form of AI D i ,T i ,τ ,which is initialized to empty.Upon receiving
A ’s query with the message (AI D i ,T i ),C checks whether a tuple AI D i ,T i ,τ exists in L h 2?rst.If so,C sends τ=h 2(AI D i ||T i )to A ;otherwise,C generates a random number τ∈Z q ,adds AI D i ,T i ,τ in L h 2and sends τ=h 2(AI D i ||T i )to A .
h 3?Oracle :C keeps a list L h 3with the form of AI D i ,T i ,R i ,M i ,τ ,which is initialized to empty.Upon receiving A ’s query with the message (AI D i ,T i ,R i ,M i ),C checks if a tuple AI D i ,T i ,R i ,M i ,τ exists in L h 3?rst.If so,C sends τ=h 3(AI D i ||T i ||R i ||M i )to A ;otherwise,C generates a random number τ∈Z q ,adds AI D i ,T i ,R i ,M i ,τ in L h 3and sends τ=h 3(AI D i ||T i ||R i ||M i )to A .Sign ?Oracle :Upon receiving A ’s query with the mes-sage M i ,C generates three random numbers σi ,αi ,βi ∈Z ?q
,chooses a random point AI D i ,2and computes AI D i ,1=σi ·P ?αi ·P pub ?βi ·R i .C adds AI D i ,T i ,αi and AI D i ,T i ,R i ,M i ,βi into L h 2and L h 3respectively,where AI D i ={AI D i ,1,AI D i ,2}.Finally,C sends the message {M i ,AI D i ,T i ,R i ,σi }to A .It is easy to verify the equation σi ·P =AI D i ,1+αi ·P pub +βi ·R i holds.Therefore,all signatures generated by C are indistinguishable from those generated by legal vehicles.
At last,A outputs a message {M i ,AI D i ,T i ,R i ,σi }.C checks whether the following equation holds.
σi ·P =AI D i ,1+αi ·P pub +βi ·R i
(4)
If it does not hold,C aborts the process.According to the forgery lemma [30],A could output another valid message {M i ,AI D i ,T i ,R i ,σ i }if we repeat the process with a different choice of h 2.In this case,we could get the following equation.
σ i ·P =AI D i ,1+α i ·P pub +βi ·R i
(5)
According to equations (4)and (5),we could get (σi ?σ i )·P =σi ·P ?σ i ·P
=AI D i ,1+αi ·P pub +βi ·R i
?(AI D i ,1+α i ·P pub +βi ·R i )
=(αi ?α i )·P pub =(αi ?α i )·x ·P
(6)and
σi ?σ i =(αi ?α i )·x mod q
(7)
C outputs (αi ?α i )?1(σi ?σ i )as the answer of the DL problem.The ability of solving the DL problem contradicts the hardness of the DL problem.Therefore,the proposed ID-based CPPA scheme for V ANETs is secure against forgery under adaptive chosen message attack in the random oracle model.
1)Message authentication :According to Theorem 1,we know that no polynomial adversary can forge a valid message if the DL problem is hard.Therefore,the veri?er could check the validity and integrity of the message {M i ,AI D i ,T i ,R i ,σi }by verifying whether the equation σi ·P =AI D i ,1+αi ·P pub +βi ·R i holds.Thus,the pro-posed ID-based CPPA scheme for V ANETs provides message authentication.
2)Preserving identity privacy :The vehicle’s real identity RI D is involved in AI D i generated by the vehicle,where
HE et al.:EFFICIENT IDENTITY-BASED CPPA SCHEME FOR V ANETs2687
P pub=x·P,AI D i,1=w i·P,AI D i,2=RI D⊕h1(w i·P pub)and AI D i={AI D i,1,AI D i,2}.To extract RI D from AI D i,2=RI D⊕h1(w i·P pub),the adversary computes w i·P pub=w i·x·P from P pub=x·P and AI D i,1=w i·P.Therefore,the adversary has to solve the CDH problem.According to the hardness of the CDH prob-lem,we conclude that the proposed ID-based CPPA scheme for V ANETs preserves identity privacy.
3)Traceability:The vehicle’s real identity RI D is involved in AI D i generated by the vehicle,where P pub=x·P, AI D i,1=w i·P,AI D i,2=RI D⊕h1(w i·P pub)and AI D i={AI D i,1,AI D i,2}.Using the private key of the system,TA computes x·AI D i,1=x·w i·P=w i·x·P= w i·P pub and extracts the real identity by computing RI D= AI D i,2⊕h1(x·AI D i,1).Therefore,the proposed ID-based CPPA scheme for V ANETs could provide traceability.
4)Un-linkability:To generate a message {M i,AI D i,T i,R i,σi},the tamper-proof device and the vehicle in the proposed ID-based CPPA scheme generates two random w i∈Z?q and r i∈Z?q separately,where AI D i,1=w i·P,AI D i,2=RI D⊕h1(w i·P pub), AI D i={AI D i,1,AI D i,2},sk i=w i+αi·x mod q,αi=h2(AI D i||T i),R i=r i·P,βi=h3(AI D i||T i||R i||M i) andσi=sk i+βi·r i mod q.Due to the randomness of w i and r i,no adversary could link two anonymous identities or two signatures generated by the same vehicle.Therefore, the proposed ID-based CPPA scheme for V ANETs provides un-linkability.
5)Resistant against various types of attacks:We show that the proposed ID-based CPPA scheme for V ANETs could withstand the impersonation attack,the modi?cation attack, the replay attack,the man-in-the-middle attack,and the stolen veri?er table attack as follows.
?Impersonation attack:To impersonate a vehicle to RSUs or other vehicles,the adversary must generate a message {M i,AI D i,T i,R i,σi}satisfying the equationσi·P= AI D i,1+αi·P pub+βi·R i.According to Theorem1, the adversary cannot generate such messages.RSUs and other vehicles could detect the attack easily by check-ing whether the above equation holds.Therefore,the proposed ID-based CPPA scheme for V ANETs could withstand the impersonation attack.
?Modi?cation attack:According to description of the proposed ID-based CPPA scheme,we know that {AI D i,R i,σi}is a digital signature of{M i,T i}.Based on Theorem1,any modi?cation of the message {M i,AI D i,T i,R i,σi}could be found by checking whether the equationσi·P=AI D i,1+αi·P pub+βi·R i holds.Therefore,the proposed ID-based CPPA scheme for V ANETs could withstand the modi?cation attack.?Replay attack:The timestamp T i is included in the message{M i,AI D i,T i,R i,σi}and{AI D i,R i,σi}is a digital signature of{M i,T i}.Then,RSUs and other vehicles could?nd the replay of the message by checking the freshness of the timestamp T i.Therefore,the proposed ID-based CPPA scheme for V ANETs could withstand the replay attack.
TABLE I
S ECURITY C OMPARISONS OF P AST S CHEMES AND
O UR P ROPOSED S CHEME
?Man-in-the-middle attack:According to the above analysis about message authentication,we know the pro-posed ID-based CPPA scheme for V ANETs could provide authentication between the sender and the receiver.
Therefore,the proposed ID-based CPPA scheme for V ANETs could withstand the man-in-the-middle attack.?Stolen veri?er table attack:Neither the RSU nor the vehicle maintains a veri?er table for message authenti-cation because they just needs to store their own private key.Then,the adversary cannot steal any veri?er table for malicious attacks.Therefore,the proposed ID-based CPPA scheme for V ANETs could withstand the stolen veri?er table attack.
B.Security Comparisons
We compare the security of our proposed ID-based CPPA scheme for V ANETs with three recently proposed ID-based CPPA schemes[20],[22],[23]for V ANETs.Let S R?1,S R?2,S R?3,S R?4and S R?5denote message authentication,preservation of identity privacy,trace-ability,un-linkability and resistance to attacks respectively. The security comparisons of the various schemes are listed in Table I.
According to Table I,none of the three schemes (i.e.,Shim’s scheme[20],Zhang et al.’s scheme[22], Zhang et al.’s scheme[23])can satisfy all5security requirements(SR-1to SR-5).Besides,Shim’s ID-based CPPA scheme[1]is not able to provide un-linkability because the vehicle’s anonymous identity is a constant.In contrast,our proposed ID-based CPPA scheme could satisfy all?ve security requirements in V ANETs.
VI.P ERFORMANCE A NALYSIS
In this section,we analyze the performance of the proposed ID-based CPPA scheme for V ANETs.We analyze both the computation cost and the communication cost in the next two subsections.Besides,we also compare the performance of the proposed ID-based CPPA scheme for V ANETs with three most recent ID-based CPPA schemes proposed in the literature. For bilinear pairings based ID-based CPPA schemes for V ANETs[20],[22],[23],we use a bilinear pairings
2688IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY,VOL.10,NO.12,DECEMBER2015 e:G1×G1→G2to achieve the security level
of80bits,where G1is an additive group generated by a
point P with the order q on the super singular elliptic curve
E:y2=x3+x mod p with embedding degree2,p is
a512-bit prime number,q is a160-bit Solinas prime number
and the equation p+1=12qr holds.For ECC-based ID-based
CPPA schemes for V ANETs(the proposed scheme),we use an
additive group G generated by a point P with the order q on
a non-singular elliptic curve E:y2=x3+ax+
b mod p
to achieve the security level of80bits,where p,q are
two160-bit prime numbers and a,b∈Z?p.
https://www.sodocs.net/doc/3a4249400.html,putation Cost Analysis
In this subsection,we analyze the computation cost of
related ID-based CPPA schemes for V ANETs.For conve-
nience,we de?ne some notations about execution time as
follows.
?T bp:the execution time of a bilinear pairing operation
e(S,T),where S,T∈G1.
?T sm?bp:the execution time of a scale multiplication
operation x·P related to the bilinear pairing,where
x∈Z?
q and P∈G1.
?T sm?bp?s:the execution time of a small scale multiplica-tion operation v i·P related to the bilinear pairing,which is used in the small exponent test,where P∈G1,v i is a small random integer in[1,2t]and t is a small integer.?T pa?bp:the execution time of a point addition operation S+T related to the bilinear pairing,where S,T∈G1.?T mtp:the execution time of a hash-to-point operation related to the bilinear pairing,where the hash function maps a string to a point of G1.
?T sm?ecc:the execution time of a scale multiplication operation x·P related to the ECC,where x∈Z?q and P∈G.
?T sm?ecc?s:the execution time of a small scale multipli-cation operation v i·P used in the small exponent test technology,where P∈G,v i is a small random integer in[1,2t]and t is a small integer.
?T pa?ecc:the execution time of a point addition operation S+T related to the ECC,where S,T∈G.
?T h:the execution time of a general hash function opera-tion.
To compare the computation cost of related ID-based CPPA schemes for V ANETs,we compute the execution time of above cryptographic operations using MIRACL[31],which is a famous cryptographic library and has been widely used to implement cryptographic operations in many environments. Our hardware platform consists of an Intel I7-4770processor with3.40GHz clock frequency,4gigabytes memory and runs Windows7operating system.The execution time of the above cryptographic operations are listed in Table II.
Let AI DG M S and SV O M and BV M M denote the anony-mous identity generation and message signing,the single ver-i?cation of one message and the batch veri?cation of multiple messages steps respectively.We only present the detailed analysis of Bayat et al.’s scheme[23]and the proposed scheme.The detailed analysis of other schemes[20],[22]could
TABLE II
E XECUTION T IME O
F D IFFERENT C RYPTOGRAPHIC O PERATIONS
be achieved using the same method.The comparisons of computation costs for each step are presented in Table III. For the AI DG M S step of Bayat et al.’s ID-based
CPPA scheme[23],the vehicle needs to execute?ve scalar multiplication operations related to the bilinear pairing,one
point addition operation related to the bilinear pairing,one hash-to-point operation related to the bilinear pairing and one general hash function operation.Therefore,the execution
time of this step is5T sm?bp+1T pa?bp+1T mtp+2T h≈12.9583ms.For the SV O M step of Bayat et al.’s ID-based CPPA scheme[23],the veri?er needs to execute three bilinear
pairing operations,one scalar multiplication operation related to the bilinear pairing,one hash-to-point operation related to the bilinear pairing and one general hash function operation. Therefore,the execution time of this step is3T bp+1T sm?bp+ 1T mtp+1T h≈18.7481ms.For the BV M M step of Bayat et al.’s ID-based CPPA scheme[23],the veri?er needs to execute three bilinear pairing operations,(n)scalar multiplication operations related to the bilinear pairing, (3n?3)point addition operations related to the bilinear pairing, (n)hash-to-point operations related to the bilinear pairing and (n)general hash function operations.Therefore,the execution time of this step is3T bp+(n)T sm?bp?s+(3n?3)T pa?bp+ (n)T mtp+(n)T h≈6.1364n+12.6117ms.
For AI DG M S step of our proposed ID-based CPPA scheme,the vehicle needs to execute three scalar multiplication operations related to the ECC and three general hash function operations.Therefore,the execution time of the step is3T sm?ecc+3T h≈1.3263ms.For the SV O M step of the proposed ID-based CPPA scheme,the veri?er needs to execute three scalar multiplication operations related to the ECC,two point addition operations related to the ECC and two general hash function operations.Therefore,the execution time of the phase is3T sm?ecc+2T pa?ecc+2T h≈1.3298ms.For the BV M M step of the proposed ID-based CPPA scheme,the veri?er needs to execute(n+2) scalar multiplication operations related to the ECC,
HE et al.:EFFICIENT IDENTITY-BASED CPPA SCHEME FOR V ANETs2689
TABLE III
C OMPARISON OF C OMPUTATION C OST
(2n)small scalar multiplication operations related to the ECC,
(3n?1)point addition operations related to the ECC and(2n)
general hash function operations.Therefore,the execution
time of this step is(n+2)T sm?ecc+(2n)T sm?ecc?s+
(3n?1)T pa?ecc+(2n)T h≈0.4252n+0.8822ms
(t=5)/0.5027n+0.8822ms(t=10).The percentage
improvement with the AI DG M S step of our proposed
scheme over Bayat et al.’s scheme for the total execution
time is about12.9583?1.3263
12.9583≈89.76%.Other percentage
improvement could be achieved by using a similar method.
To demonstrate the major bene?t of the proposed ID-based CPPA scheme in the batch veri?cation of multiple messages, we compare the execution times of batch veri?cation in the proposed scheme with three most recently proposed
ID-based
Fig.3.Execution time for the batch veri?cation of multiple messages.
TABLE IV
C OMPARISON OF C OMMUNICATION C OST
CPPA schemes[20],[22],[23]as shown in Figure3.Based on the results shown in Table III and Figure3,the proposed ID-based CPPA scheme for V ANETs has lower computation cost compared to the three most recently proposed ID-based CPPA schemes for V ANETs for all three steps including AI DG M S,SV O M,and BV M M.
https://www.sodocs.net/doc/3a4249400.html,munication Cost Analysis
In this subsection,we analyze the communication cost of related ID-based CPPA schemes for V ANETs.Since the sizes of p and p are64bytes(512bits)and20bytes(160bits) respectively,then the sizes of the elements in G1and G are 64×2=128bytes and20×2=40bytes respectively. Besides,let the sizes of the general hash function’s output and timestamp be20bytes and4bytes respectively.We only consider the size of signature because messages about traf?c status are the same in all ID-based CPPA schemes.The comparison of computation costs is presented in Table IV.
In the Shim’s ID-based CPPA scheme[20],the vehi-cle broadcasts the anonymous identity and signature {AI D i,T i,U i,V i,W i}to the veri?er,where AI D i= {AI D1i,AI D2i},AI D1i,AI D2i,U i,V i,W i∈G1and T i is the
timestamp.Therefore,the communication cost of the Shim’s ID-based CPPA scheme[20]is128×5+4=644bytes. In the Zhang et al.’s ID-based CPPA scheme[22]and Bayat et al.’s scheme[23],the vehicle broadcasts the anony-mous identity and signature{AI D i,T i,U i}to the veri?er, where AI D i={AI D1i,AI D2i},AI D1i,AI D2i,U i∈G1 and T i is the timestamp.Therefore,the communication cost of Zhang et al.’s ID-based CPPA scheme[22]is 128×3+4=388bytes.The vehicle in the proposed CPPA scheme broadcasts the anonymous identity and sig-nature{AI D i,T i,R i,σi}to the veri?er,where AI D i= {AI D1i,AI D2i},AI D1i,AI D2i,R i∈G,σi∈Z q and T i is the timestamp.Therefore,the communication cost of the proposed CPPA scheme is40×3+20+4=144bytes.
2690IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY,VOL.10,NO.12,DECEMBER2015
Thus,the proposed CPPA scheme for V ANETs incurs a much lower communication cost than the three latest ID-based CPPA schemes for V ANETs[20],[22],[23].
VII.C ONCLUSION
In this work,we have proposed a new ID-based CPPA scheme,which could be used for both V2V commu-nication and V2I communication in V ANETs.To improve performance,the function of batch veri?cation of multiple messages is included in the proposed ID-based CPPA scheme. The security analysis shows that the proposed scheme can overcome the weaknesses of previously proposed schemes and satisfy the security requirements of ID-based CPPA schemes for V ANETs.Our performance analysis results show that the proposed scheme incurs lower computation cost and communication cost because no bilinear pairings are used in our proposed ID-based CPPA scheme.This makes the proposed scheme more suitable for deployment in the V ANET environment.
A CKNOWLEDGMENT
The authors thank the Associate Editor and the anonymous reviewers for their useful comments and suggestions which helped us improve the quality and presentation of this paper.
R EFERENCES
[1]T.W.Chim,S.M.Yiu,L.C.K.Hui,and V.O.K.Li,“SPECS:
Secure and privacy enhancing communications schemes for V ANETs,”
Ad Hoc Netw.,vol.9,no.2,pp.189–203,2011.
[2]S.Zeadally,R.Hunt,Y.-S.Chen,A.Irwin,and A.Hassan,“Vehic-
ular ad hoc networks(V ANETs):Status,results,and challenges,”
Telecommun.Syst.,vol.50,no.4,pp.217–241,2012.
[3]M.Ghosh,A.Varghese,A.Gupta,A.A.Kherani,and S.N.Muthaiah,
“Detecting misbehaviors in V ANET with integrated root-cause analysis,”
Ad Hoc Netw.,vol.8,no.7,pp.778–790,2010.
[4]Y.Toor,P.Muhlethaler,and https://www.sodocs.net/doc/3a4249400.html,ouiti,“Vehicle ad hoc networks:
Applications and related technical issues,”IEEE Commun.Surveys Tuts., vol.10,no.3,pp.74–87,Sep.2008.
[5] A.Boukerche,H. A. B.FOliveira, E. F.Nakamura,and
A. A. F.Loureiro,“Vehicular ad hoc networks:A new challenge
for localization-based systems,”https://www.sodocs.net/doc/3a4249400.html,mun.,vol.31,no.12, pp.2838–2849,2008.
[6]IEEE Trial-Use Standard for Wireless Access in Vehicular
Environment—Security Services for Applications and Management Messages,IEEE Standard1609.2-2006,Jul.2006.
[7]M.Raya,P.Papadimitratos,and J.-P.Hubaux,“Securing vehicular
communications,”IEEE Wireless Commun.,vol.13,no.5,pp.8–15, Oct.2006.
[8]J.T.Isaac,S.Zeadally,and J.S.Camara,“Security attacks and
solutions for vehicular ad hoc networks,”IET Commun.J.,vol.4,no.7, pp.894–903,2010.
[9]J.P.Hubaux,S.Capkun,and J.Luo,“The security and privacy of
smart vehicles,”IEEE Security Privacy,vol.2,no.3,pp.49–55, May/Jun.2004.
[10] C.Gamage,B.Gras,B.Crispo,and A.S.Tanenbaum,“An identity-
based ring signature scheme with enhanced privacy,”in Proc.
Securecomm Workshops,2006,pp.1–5.
[11]M.Raya and J.-P.Hubaux,“Securing vehicular ad hoc networks,”
https://www.sodocs.net/doc/3a4249400.html,put.Secur.,vol.15,no.1,pp.39–68,2007.
[12]R.Lu,X.Lin,H.Zhu,P.-H.Ho,and X.Shen,“ECPP:Ef?cient
conditional privacy preservation protocol for secure vehicular commu-nications,”in Proc.27th Conf.IEEE INFOCOM,Apr.2008,pp.1903–1911.
[13]J.Freudiger,M.Raya,M.Felegyhazi,and P.Papadimitratos,“Mix-zones
for location privacy in vehicular networks,”in Proc.1st Int.Workshop Wireless Netw.Intell.Transport.Syst.(Win-ITS),2007,pp.1–7.[14] C.Zhang,X.Lin,R.Lu,and P.-H.Ho,“RAISE:An ef?cient RSU-aided
message authentication scheme in vehicular communication networks,”
in Proc.ICC,May2008,pp.1451–1457.
[15] C.Zhang,R.Lu,X.Lin,P.-H.Ho,and X.Shen,“An ef?cient identity-
based batch veri?cation scheme for vehicular sensor networks,”in Proc.
IEEE INFOCOM,Apr.2008,pp.816–824.
[16] C.Zhang,P.-H.Ho,and J.Tapolcai,“On batch veri?cation with group
testing for vehicular communications,”Wireless Netw.,vol.17,no.8, pp.1851–1865,2011.
[17] A.Shamir,“Identity-based cryptosystems and signature schemes,”in
Proc.CRYPTO,1984,pp.47–53.
[18] C.-C.Lee and https://www.sodocs.net/doc/3a4249400.html,i,“Toward a secure batch veri?cation with group
testing for V ANET,”Wireless Netw.,vol.19,no.6,pp.1441–1449,2013.
[19]S.-J.Horng et al.,“b-SPECS+:Batch veri?cation for secure pseudony-
mous authentication in V ANET,”IEEE Trans.Inf.Forensics Security, vol.8,no.11,pp.1860–1875,Nov.2013.
[20]K.-A.Shim,“CPAS:An ef?cient conditional privacy-preserving authen-
tication scheme for vehicular sensor networks,”IEEE Trans.Veh.
Technol.,vol.61,no.4,pp.1874–1883,May2012.
[21]J.K.Liu,T.H.Yuen,M.H.Au,and W.Susilo,“Improvements on
an authentication scheme for vehicular sensor networks,”Expert Syst.
Appl.,vol.41,no.5,pp.2559–2564,2014.
[22]J.Zhang,M.Xu,and L.Liu,“On the security of a secure batch
veri?cation with group testing for V ANET,”https://www.sodocs.net/doc/3a4249400.html,w.Secur.,vol.16, no.5,pp.355–362,2014.
[23]M.Bayat,M.Barmshoory,M.Rahimi,and M.R.Aref,“A secure
authentication scheme for V ANETs with batch veri?cation,”Wireless Netw.,vol.21,no.5,pp.1733–1743,2015.
[24] D.Freeman,M.Scott,and E.Teske,“A taxonomy of pairing-friendly
elliptic curves,”J.Cryptol.,vol.23,no.2,pp.224–280,2010. [25]X.Cao,W.Kou,and X.Du,“A pairing-free identity-based authenticated
key agreement protocol with minimal message exchanges,”Inf.Sci., vol.180,no.15,pp.2895–2903,2010.
[26]L.Zhang,Q.Wu, A.Solanas,and J.Domingo-Ferrer,“A scalable
robust authentication protocol for secure vehicular communications,”
IEEE Trans.Veh.Technol.,vol.59,no.4,pp.1606–1617,May2010.
[27]L.Zhang,Q.Wu,B.Qin,and J.Domingo-Ferrer,“APPA:Aggregate
privacy-preserving authentication in vehicular ad hoc networks,”in Proc.14th Conf.Inf.Secur.(ISC),2011,pp.293–308.
[28]X.Lin,X.Sun,P.-H.Ho,and X.Shen,“GSIS:A secure and privacy-
preserving protocol for vehicular communications,”IEEE Trans.Veh.
Technol.,vol.56,no.6,pp.3442–3456,Nov.2007.
[29] C.P.Schnorr,“Ef?cient signature generation by smart cards,”
J.Cryptol.,vol.4,no.3,pp.161–174,1991.
[30] D.Pointcheval and J.Stern,“Security arguments for digital signatures
and blind signatures,”J.Cryptol.,vol.13,no.3,pp.361–396,2000.
[31]Shamus Software Ltd.MIRACL Library.[Online].Available:
http://www.shamus.ie/index.php?page=home,accessed May1,
2015.
Debiao He received the Ph.D.degree in applied
mathematics from the School of Mathematics
and Statistics,Wuhan University,Wuhan,China,
in2009.He is currently an Associate Professor with
the State Key Laboratory of Software Engineering,
School of Computer Science,Wuhan University.
His main research interests include cryptography
and information security,in particular,cryptographic
protocols.
Sherali Zeadally received the bachelor’s degree in
computer science from the University of Cambridge,
U.K.,and the Ph.D.degree in computer science
from the University of Buckingham,U.K.He is
currently an Associate Professor with the College
of Communication and Information,University of
Kentucky,Lexington,KY,USA.He is also a fellow
of the British Computer Society and the Institution
of Engineering Technology,U.K.
HE et al.:EFFICIENT IDENTITY-BASED CPPA SCHEME FOR V ANETs
2691
Baowen Xu(M’03)received the B.S.degree from Wuhan University,the M.S.degree from the Huazhong University of Science and Technology, and the Ph.D.degree from Beihang University,all in computer science.He is currently a Professor with the Department of Computer Science and Technol-ogy,Nanjing University.His main research interests include programming languages,software testing, software maintenance,and software metrics.He is a member of the IEEE Computer
Society.
Xinyi Huang received the Ph.D.degree from the
School of Computer Science and Software Engineer-
ing,University of Wollongong,Australia.He is cur-
rently a Professor with the School of Mathematics
and Computer Science,Fujian Normal University,
China,and the Co-Director of the Fujian Provincial
Key Laboratory of Network Security and Cryptol-
ogy.He has authored over100research papers in
refereed international conferences and journals.His
work has been cited more than1900times at Google
Scholar(H-Index:25).His research interests include applied cryptography and network security.He is also an Associate Editor of the IEEE T RANSACTIONS ON D EPENDABLE AND S ECURE C OMPUTING,and on the Editorial Board of the International Journal of Information Security (IJIS,Springer).He has served as the Program/General Chair or Program Committee Member in over60international conferences.
福建省福州格致中学2014-2015学年高一上学期期中考试英语试题 Word版无答案
福州格致中学2014-2015学年第一学段 高一英语《必修一》模块考试 第二部分:英语知识运用 单项填空 从每题所给的A、B、C、D四个选项中,选出可以填入空白处的最佳答案,并在答题卡上将该选项涂黑。 21.In _______ distance is a tall tree which is said to have ______ history of over 500 years. A. the; a B. /; / C. a; a D. the; / 22.--- Look! The telephone is broken. Someone damaged it _______ purpose. --- That may be right. But perhaps it was broken ________ accident. A. on; on B. on; by C. by; by D. by; on 23.It might be very difficult to find _______ of the information. A. cause B. resource C. source D. course 24. Shall we go there by bus or by taxi? The ______ seems to be quicker. A. late B. latter C. later D. lately 25. After living in the United States for fifty years, he returned to the small town where he ______. A. brought up B. grew up C. gave up D. turned up 26. The engine of the ship was out of order and the bad weather ________ the helplessness of the crew(船员) at sea. A. added to B. added up to C. added up D. was added to 27. --- Daddy, I don’t want to go to Jimmy’s birthday. --- You had better go. ______ you make a promise, you have to keep it. A. Even B. Once C. Unless D. In case 28. --- Won’t you stay for lunch? --- No, thanks, I _______ my uncle at the airport at 10:30. A. met B. have met C. meet D. am meeting 29. ________ out for food, Some work in the nest as guards or workers. A. All the bees not go B. Both the bees don’t go C. Not all the bees go D. All the bees go 30. The old town has narrow streets and small houses _______ are built close to each other. A. they B. where C. what D. that 31. --- Don’t you know our town at all? --- No, It is the first time I _______ here. A. was B. am coming C. came D. have come 32. Can you make sure _____ the gold ring? A. where Alice had put B. where had Alice put C. where Alice has put D. where has Alice put 33. He decided to help the poor girl _______ were killed in the earthquake. A. which parents B. parents of them C. whose parents D. whom parents 34. The settlement is home to nearly to 1,000 people, many of _______ left their village homes for a better life in the city. A. whom B. which C. them D. who 35. ---We could invite John and Barbara to the Friday night party. --- Yes, _______ ? I’ll give them a call right now. A. why not B. what for C. why D. what 第二节完形填空(共20 小题;每小题一分,满分20分) 阅读下面短文,从短文后各题所给的四个选项(A,B,C,D)中选出可以填入相应空白处的最佳选项,并在答题卡上将该选项涂黑。 This little story I’m going to tell you happened when I was about 11 years old and I’II never forget it. I was at my friend Jenny’s __36__ after school one day, and we were doing (or not doing) homework.. __37__ I was there, Jenny’s mom came over to visit. I don’t remember her name__38__ what her face looked like. I just remember her hands, her voice and the__39__ she taught me. I can still see her hand __40__ for mine in our introduction. __41__ were so
尊重的素材
尊重的素材(为人处世) 思路 人与人之间只有互相尊重才能友好相处 要让别人尊重自己,首先自己得尊重自己 尊重能减少人与人之间的摩擦 尊重需要理解和宽容 尊重也应坚持原则 尊重能促进社会成员之间的沟通 尊重别人的劳动成果 尊重能巩固友谊 尊重会使合作更愉快 和谐的社会需要彼此间的尊重 名言 施与人,但不要使对方有受施的感觉。帮助人,但给予对方最高的尊重。这是助人的艺术,也是仁爱的情操。—刘墉 卑己而尊人是不好的,尊己而卑人也是不好的。———徐特立 知道他自己尊严的人,他就完全不能尊重别人的尊严。———席勒 真正伟大的人是不压制人也不受人压制的。———纪伯伦 草木是靠着上天的雨露滋长的,但是它们也敢仰望穹苍。———莎士比亚 尊重别人,才能让人尊敬。———笛卡尔 谁自尊,谁就会得到尊重。———巴尔扎克 人应尊敬他自己,并应自视能配得上最高尚的东西。———黑格尔 对人不尊敬,首先就是对自己的不尊敬。———惠特曼
每当人们不尊重我们时,我们总被深深激怒。然而在内心深处,没有一个人十分尊重自己。———马克·吐温 忍辱偷生的人,绝不会受人尊重。———高乃依 敬人者,人恒敬之。———《孟子》 人必自敬,然后人敬之;人必自侮,然后人侮之。———扬雄 不知自爱反是自害。———郑善夫 仁者必敬人。———《荀子》 君子贵人而贱己,先人而后己。———《礼记》 尊严是人类灵魂中不可糟蹋的东西。———古斯曼 对一个人的尊重要达到他所希望的程度,那是困难的。———沃夫格纳 经典素材 1元和200元 (尊重劳动成果) 香港大富豪李嘉诚在下车时不慎将一元钱掉入车下,随即屈身去拾,旁边一服务生看到了,上前帮他拾起了一元钱。李嘉诚收起一元钱后,给了服务生200元酬金。 这里面其实包含了钱以外的价值观念。李嘉诚虽然巨富,但生活俭朴,从不挥霍浪费。他深知亿万资产,都是一元一元挣来的。钱币在他眼中已抽象为一种劳动,而劳动已成为他最重要的生存方式,他的所有财富,都是靠每天20小时以上的劳动堆积起来的。200元酬金,实际上是对劳动的尊重和报答,是不能用金钱衡量的。 富兰克林借书解怨 (尊重别人赢得朋友)
春风拂面范文
春风拂面 每每想起老师,仿佛总有一股春风从面前拂过。它那样温暖,那样和煦,像润物无声的细雨,慢慢地催开了我心底那美丽的花儿。 老师,您是否还记得那次午休?同学们都伏在课桌上睡觉,后来外面下起了雨,阵阵凉凉的风吹进教室,吹乱了您的头发,也吹乱了同学的衣裳。您正想起身做点什么,突然您好像想起了什么,又坐了下来——噢!只见您脱下了您的高跟鞋,轻轻地走到窗户边,悄悄地把每一扇窗户都关上了。啊!老师,您是怕吵醒了那些可爱的熟睡的孩子呀!老师,您知道吗?那一刻,我觉得自己就像是一个孩子,生活在母亲的怀抱。那一刻,我觉得您就像一 股春风,悄悄从我们身边吹过。 老师,您可曾想起那个炎热的下午?我们在楼梯口相遇,我道了一句“老师好”,您甜甜一笑,走过来,轻轻地拉了拉我的衣领:“热不热?”突然,您发现我的脖子上那些红肿的小疱,您关切地问:“呀!这是怎么回事,蚊子咬的吗?”我点了点头。没想到第二天早上,您就给我带来了驱蚊花露水。那一刻,我又惊讶又感动。望着同学们羡慕的眼光,我的心底仿佛拂过一缕春风,温暖而幸福。 老师,您是否记得那次晨读?同学们都在教室里认真地读书,忽然,我感觉有个身影从我身旁走过。一抬头,我才发现桌子上多了一瓶牛奶,上面还有几个有趣的字“喝了长高噢”。再朝那个身影望去——乌黑笔直的秀发飘在肩后,我知道,是老师您。 老师!您知道吗?在住校的那段时间,我时常会记起您,我时常会抱着那花露水瓶子睡觉,我时常会穿着您送我的带着香味的衣裳…… 一阵春风轻轻拂过,我仿佛又看到了您那熟悉的身影。 春风拂面 岁月是爱人的,每年,即使春已逝去,也会在某一个时候给人以春风拂面的感动。 我平时喜欢写作文,语文老师就鼓励我向报刊投稿。“我?能行吗?”看着老师坚定的眼睛,我下定了决心。但是一次又一次的石沉大海,我又开始灰心了。 “来,文章见报了……”声音温和,是语文老师。似乎早有预感,庆幸却又疑惑。我已忘了自己还死僵僵地坐在座位上。老师满脸笑容地离开了。“真没礼貌!”身旁的男生嘀咕道。这才醒悟:我,就是一个忽视了最简单的礼貌的人。 仿佛为我的坏心情应景一般,风儿大了,调皮地飞驰而过,掠走了我的微笑。上课后,老师就就一些难题向我们指点迷津。教材第110页……”黑板上显现出一行醒目的大字。还没等老师说完,我就心急火燎地开始复制克隆,笔走龙蛇。不料被老师撞见,批评了一句:“做题时要看清题目,再去对照答案……当时,真是无地自容,还是科代表呢!名不副实。这才明白:我,就是一个冒冒失失的人。 下课的时候,狂风骤起,刹那间将我无奈的寂寞卷入云层。学习上的退步,甚至让我怀疑自己就是一个超低智商的人。于是,一次次地摔跤、失落、放弃、流泪。感觉生活就是一座幽深的城堡,欲离去却始终找不着方向。可是,在晚饭时,当妈妈把熟悉的饭盒递到我手中,接着是匆忙的问候,我忘记了吃饭,那一刻,忽然感觉到如春风拂面,幸福无比。 我总是这样,预先准备了对待苦难的从容,却没学会从苦难中体验快活,总是注重自己的感受,却忽视了身边一直伴随提醒我的亲人朋友。同学的良言规劝是幸福,老师的悉心开导是幸福,亲人馈赠的欣悦是幸福……这样的幸福太多太多。 一路上,被人提醒,如沐春风。 [点评]这篇文章在选材时注重了“小处着眼”,写生活中时时处处有人提醒:忽视礼节,冒冒失失,忘记吃饭,这些琐碎的生活片段,写出了对生活深层次的感悟,紧扣“提醒”,揭示主题:原来,生活中有了提醒,是一种莫大的幸福。 春风拂面 春风,在我心目中是最纯洁、最高尚的。它从容淡定、缥缈虚无,同时又是世间自由不羁的精神所在,亦如那些从历史里缓缓走来的身影…· 那不羁的风,我想,是李白吧!他有"飞流直下三千尺,疑是银河落九天"的气魄,他有"仰天大笑出门去,我辈岂是蓬蒿人"的潇洒,他有"安能摧眉折腰事权贵,使我不得开心颜"
小学语文《想象作文》教案设计之一
小学语文《想象作文》教案设计之一 小学语文《想象作文》教案设计之一 一、教学目的 1.启发学生自由地想象,培养学生的创新思维能力。 2.指导学生有序地、重点突出地、主次分明地说和写。 3.培养学生热爱学校、热爱生活、热爱科学的思想感情。 二、教学重点 启迪学生展开大胆、丰富、新奇的想象,并指导学生有序地、主次分明地说和写。 三、课前准备 1.课前学生绘制自己心目中《未来的......》构想图。 2.制作多媒体课件。 四、教学时间 二课时(第二课时为写作及讲评) 五、教学过程 第一课时 (一)导入
1.谈话:(出示课件1后)小的时候,我就曾经幻想过,如果我能够像小鸟一样,有那样一对翅膀,那该多好啊!现在你们又有怎样的想象呢?(板书:想象) 2.结合学生回答表扬“你的想象真大胆!”.“你的想象真丰富!”.“你的想象真新奇!”(教师板书:大胆.丰富.新奇) 3.小结:希望同学们能把大胆.丰富.新奇的想象,在自己的作文中体现出来。(4分钟) (二)本次作文指导经过。 1.让我们乘上宇宙飞船,穿越时空隧道,去未来看一看吧!(出示课件2)(1分钟) 2.我们还在去未来的路上,但是伟大的科学家爱因斯坦曾经说过:“想象是一切创造之源。”(出示课件3)这节课让我们用想象创设一下未来吧!同学们,今天这节课,我们就来写一写未来的......(板书:未来的......)(出示课件4)(1分钟) 1.读一下课题,你觉得可以写什么?进行讨论。(3分钟) 提示:人物、事物、军事、科技、农业、环境、体育等等。 估计可能有的题目:《未来的我》、《未来的生日》、《未来的母校》、《未来的教师》、《未来的祖国》,以及《未来的地球》、《未来的汽车》、《未来的学校》。 明确:在现实生活的基础上,随着科技发展,将来可能实现的设想或可能拥有的事物才可写。 2.我们选好了要写的题目,那么怎么来写,具体写些什么呢? 3.学习小组进行讨论,要求:
福建省福州格致中学高考英语备考听力训练二十五试题 含答案
25. 第一部分听力(共两节。满分30分) 第一节(共5小题;每小题l.5分,满分7.5分) 听下面5段对话。每段对话后有一个小题,从题中所给的A、B、C三个选项中选出最佳选项,并标在试卷的相应位置。听完每段对话后,你都有l0秒钟的时间来回答有关小题和阅读下一小题。每段对话仅读一遍。 1.What is the probable relationship between the speakers? A. Father and daughter. B. Doctor and patient. C. Teacher and student. 2.Why can’t the machine work according to the woman? A.The power may have been cut off. B.There is something wrong with it. C.Both of the speakers can’t operate it. 3.What does the woman mean? A She is tired of keeping pets. B She wants to have a dog. C She won’t have a dog as a friend. 4.What can we learn from the conversation? A.The man will invite Mary to dinner. B The man will buy his daughter a gift. C.Mary has a lovely girl. 5.Which of the following does the woman like best? A. Fishing.13.Swimming.C.Climbing. 第二节(共15小题;每小题l.5分,满分22.5分) 听下面5段对话或独白。每段对话或独自后有几个小题,从题中所给的A、B、C 三个选项中选出最佳选项,并标在试卷的相应位置。听每段对话或独白前,你将有时间阅读各个小题,每小题5秒钟;听完后,各小题将给出5秒钟的作答时间。每段对话或独自读两遍。 听第6段材料。回答第6,7题。 6.What season is it now? A Spring. B Summer. C Autumn. 7.What will the speakers do? A. Drive to San Diego. B.Have take—away food in the park. C. See an outdoor movie. 听第7段材料。回答第8,9题。 8.What color is the tie the man is looking for? A. Green. B. Blue. C. Brown.
三年级下册语文第五单元作文《奇妙的想象》
三年级下册语文第五单元作文《奇妙的想象》写作指导 一、审题 写一个想象故事。展示自己的奇妙想象,创造出属于自己的想象世界。 二、选材 写想象的故事。,而不是现实生活中的事,如矮人国的故事、大熊开面馆的故事、小狗变巨人、我有魔法了……只要是你能想到的故事都可以。 三、构思 我们以《最好玩的国王》为例进行构思,简要列出习作提纲。 开头:交代国王的爱好:微服私访。(略) 中间:微服私访时发现了一本畅销书,他大受启发,自己也写了一本书,后来这本书也非常畅销。(详) 结尾:交代畅销的原因:这本书太无聊,人们买来治疗失眠。(略) 四、表达 ①为习作起一个有趣的名字,如《播种女巫》:②大胆想象,让想象的内容神奇、有趣;③记得上自己平时积累的一些好词佳句哟!
写作素材 一、题目 《瞌睡虫多多》《小豆苗历险记》《白雪公主后传》《月亮又瘦了》 二、好词 无影无踪大摇大摆活灵活现转瞬即逝 神秘莫测窃窃私语一模一样大吃一惊 远走高飞 三、好句 开头 1.晚上,一道金光闪过,我突然发现睡在身边的妹妹变成了一个巨大的金蛋。我急坏了,怎么才能把妹妹救出来呢?把蛋砸破,可能会伤到里面的妹妹。把蛋刹开妹妹会不会变成蛋清流出来呢?我想了又想,最后决定把妹妹从蛋里孵 出来。 2.在离天河不远的地方,有三颗小星星。说来也巧,这三颗小星星是同年、同月、同日、同时生的,可它们彼此都不一样:一颗是蓝的,一颗是红的,第三颗最小,似乎没有什么颜色,只有一点儿微弱得可怜的光。 结尾 1.从此,绿森林里多了一个永久性的居民,绿森林的动物们多了一个永远的朋 友,绿森林的故事里多了一份传奇。 2.大力士风孩子回来了,呼呼吹了几口气,白烟被吹跑了,烟筒和房子被吹倒了那几个黑衣人被吹到了森林外。大树们开心地笑了。
福建省福州格致中学(鼓山校区)高一英语上学期第五次月考(期末)试题
福州格致中学2015级高一学段第一学期质量评定 高一年级第五次月考英语试卷 时间:100分钟分值120分 ★祝考试顺利★(完型填空启用备用卷题号不同答题卡区域注意区别) 第Ⅰ卷选择题(共两部分,满分70分) 第一部分阅读理解(共两节,满分40分) 第一节、完形填空(共20小题;每小题1.5分,满分30分) 阅读下面短文,从短文后所给各题的四个选项(A、B、C和D)中,选出可以填入空白处的最佳选项。 Most of us are highly aware of various channels through which we can obtain information on food safety. A majority of us have shown much __36___ in experts and authorities and taken a(n) __37___ part in science activities organized by such experts. __38_, we do not always form an accurate picture When there is __39_news about one brand, our trust in all brands or similar products tends to be __40___ . We would doubt not only the brand in __41___ but also similar brands when a safety issue (问题)_42___ in the news. At the same time,our purchase __43___ change as food safety incidents occur. We are becoming _44___ confident in domestic(国内的)food companies ,for they have done too little in publishing and sharing food safety __45__ so far. As a result ,we would turn to __46__ brands more often. Food safety incidents in China have attracted a lot of attention. As a matter of fact ,we only have a very _47__ knowledge base on the issue. In developed countries,there have been relatively _48__ measures and response system toward safety issues. Therefore, the __49___ in those countries are less likely to become over-panicked and form serious _50 about all brands. Food companies should pay more attention to our insights, listen to our voices, _51___ the opinions of experts and authorities ,have effective strategies for response _52____ various media channels, and __53___ information in time and face the public honestly. In addition ,both the government and an independent third - party should have a role to play in providing information about food companies__54___ in raw material selection, production and distribution (流通) However, this might require several years and we still need to learn more about food __55___ 36. A. respect B.enthusiasm C. distrust D. confidence 37. A. slight B. broad C. active D. natural 38. A. However B. Consequently C. Meanwhile D. Furthermore 39. A. negative B. exciting C. detailed D. special 40. A. protected B. affected C. increased D. preserved
关于春风的作文(6篇)
关于春风的作文(6篇) 【第1篇】关于春风的作文:春风赞 所谓的春风,如此温柔。瞧!春风轻吻着柳枝,柳枝有节奏地摇摆着,摆动着它那细腻的腰姿,微微地吹皱了水面,偷偷地传送着花香。如此温柔、如此温柔,就像万物的母亲,无微不至地亲切体贴着万物,让万物生机勃勃地活动着。微风吹拂着千万条嫩黄色的柳枝,为它们换上了新衣裳;迎春话、牡丹花……春风吹拂着那娇媚的花儿,人们不由得分外爱惜! 一切万物只因它! 它就像一位慈祥而细心的“母亲”,她辛勤地培育着“儿女”,用她那甜美的乳汁来赋予营养给儿女,为的是什么呢?她为的是给儿女更好的东西、更好的生活和更好的体魄。儿女长大了,母亲给了他们最好的教育和贴心的爱护。如今儿女已经可以挣脱开母亲的怀抱,展翅飞翔,翱翔在天空中,那这些功劳归功于谁呢?一切都是母亲在儿女的背后默默支持的结果。 春风仿佛是一种生命的动力,它可以唤醒万物,也可以成为人的力量。春风扑面而来,使我想起了“一年之季在于春”春给人带来了新的一年,新的希望,新的人生目标……一阵春风吹来,我的头脑顿时清醒了,明白了人不仅要学,还要懂得运用。用春风来唤醒自己心中的渴望,让它告诉自己应该努力发奋,为自己的渴望而发奋实现
这美好的愿望。所以我们要珍惜这种源之动力之风。 春风如此温柔、如此细腻,怎能不让人心动去珍惜呢?让我们一起珍惜这股动力之风吧! 【第2篇】关于春风的作文:春风拂面 春天来了,太阳公公擦擦自己的眼,戴上眼镜,俯瞰世界,感叹:“这会是美好的一天。”风姑娘轻悄悄地来到了人间,用手轻抚柳树姑娘的头发,柳树姑娘醒来了,才发现这时的头发被某人梳理了一下,风姑娘摸着小草的头,轻声说:“该起床了!”这时,小草睡眼惺忪的睁开了眼睛,伸了伸懒腰。不一会儿,世间万物都从睡梦中醒来了。 她在床上熟睡,“起来,快起来!”闹钟好不耐烦的叫着,她醒了来“哎!好梦就这样被破坏了!”迅速的穿好衣服,急匆匆地走到了学校。她从书包里拿出书,大声朗读书中的内容,读着读着,就觉得有点困,本想伏在桌上休息的,她看到成绩比较好的来到了教室,她于是从书包里来翻到有问题的一页,走到他们面前寻求解题思路,问题进一步得到解决。此时春风拂面,振作了他疲惫的精神。 他和同学坐在一起,它却只能沉默过眼地陪伴这同学,他深感歉疚,同学忍不住要和他讲话,她在旁边认真地听,认真的回答他们提出问题,把心中的烦恼全部说出来了。心中舒服了好一阵子。这时春风拂面,排除了她心中的烦恼,则多了一份快乐。 从窗外望——处处都充满绿色,五彩缤纷的花点缀着绿,小鸟
小学语文想象类作文的构思技巧整理
小学语文想象类作文的构思技巧整理 给文字插上想象的翅膀,想象类作文的构思技巧整理! 学生在作文时,往往觉得没有合适的素材可写,或是不知从何想象。其实呢,不是生活中没有作文素材,而是学生缺少善于捕捉作文素材的能力。连素材都有限,自然就很难展开想象了。因此,培养学生的观察生活的能力,养成留心观察周围事物的习惯显得十分重要。 01 怎样指导孩子观察呢? 1.观察周围尽可能看到的所有事物,捕捉典型材料。 孩子的视线往往局限于一个小圈子,觉得一些司空见惯的小事没什么可写的。其实,平常的小事也可写出新意来。要选择最佳的观察对象,安排合理的观察顺序,认真观察。2.动用多种感官,丰富写作素材。 心理学认为,观察是思维的知觉,没有思维的观察是肤浅的,不是真正的观察。观察不仅仅是看,要动用耳、口、鼻、手、脑等感官去多方面地感知或判断,获得真实、全面、深刻的印象,为作文提供丰厚的材料。3.填写观察记录,养成观察习惯。 观察不应只是一次作文之前的例行公事。还应填写观察记录(观察顺序、观察方法)。 02 如何构思 以《卖火柴的小女孩》为例题,小女孩五次擦燃火柴所看到的奇异景象是作者的想象。这些想象奇特而大胆,而读者仍然觉得合情合理。
为什么呢?因为作者亲眼目睹了穷苦孩子的悲惨遭遇,深深地理解他们的内心需求。在文章中,想象与现实有着相似的地方,那就是穷孩子对幸福生活的渴望。 作者想象小女孩在神志不清时见到了温暖的火炉,喷香的烤鹅,美丽的圣诞树,慈祥的奶奶并和奶奶一起飞走,就显得自然而合理了。 无论写哪类想象作文,我们都必须做到以现实生活为基础,想象要合理、丰富,表达要真实、具体。 03 以现实生活为基础 现实生活是我们想象的源泉,离开了现实生活,想象就如同空中楼阁,成为无本之木、无源之水,变成空想或幻想。 所以,写想象作文必须勤于观察,丰富自己的生活,积极思考,驰骋想象,创新思维,这样才能引发你进行写作的灵感,进而写出优秀的想象作文。 04 怎样做到想象合理、丰富呢 1.再现 侧重于写景状物或叙事的想象作文,可以搜寻脑海中对相关事物的印象,加以再现。2.移植 有时候,想象可以进行嫁接、移植,把优美的景色移为一处,或把有趣的现象归为一物,或把美好的品质浓缩在一人之身。即,学生可以按自己的意愿中的特定形象,结合生活实际,进行移植想象。只有善于把想象与现实生活中的事实联系起来,巧妙地设计人物之间的关系,才能使文章生动有趣。3.幻想
一缕春风拂面来600字作文三篇(最新)
春风送暖,如丝般的触感滑过脸际,送来温暖的气息。像圣洁的天使飘落的羽毛,又似冬日的火光映照着脸颊,勾起心底潜藏着的那暖暖的记忆。 “怦”,好险,好险。将将赶上这班车,不然,可又得等上半小时呢! “呼”,长舒一口气,抓好扶手。提着袋子,心头嘟囔:大夏天的还得去给表弟送书,什么世道,补课竟然都不带书,学的好才怪!心里愤愤的咒骂着。 “喂,我说这个女生,不想买票哟!”售票员不耐的声音总算唤回了我的神思。吐吐舌头,开始找钱包、掏钱、买票。等等!我钱包呢?糟了,莫不是跑得急忘在家里了?! 天哪,别开玩笑了。不过很可惜,上帝爷爷今天似乎睡觉去了,我全身上下摸不出一毛钱。 售票员看着我着急的样子冷笑着:“你这样的学生我见多了,什么‘钱包没带’‘钱掉了’的,我听得多了。小小年纪什么不学,学人家坐霸王车,害不害羞哟。撒起慌来脸都不红,羞不羞!” 我长这么大,什么时候被这样当众骂过。委屈的泪水一下子涌上了眼眶:“阿姨,对不起,我下车总行了吧。” “哟,装撒。现在的小孩哟,太会演了,怕是都已经到了要去的地方了吧。” 我咬着唇,拼命忍住眼里酸涩的泪水,自知理亏,也没办法反驳。 “阿姨,她是个女生,不过忘了带钱嘛,谁不没有点难处。你话也不能这样说啊。不就一块五嘛,我帮她买了。” 闻言侧头,身边是个和我差不多大的男孩儿。看着我,他轻轻眨了眨眼。清澈的目光既像关心,又像安慰,却更像春风拂过面庞,在炎炎夏日里带来阵阵温暖的清凉。眼里充盈的泪水,在此时,落了。 “谢谢,你叫什么名字。”我低低道着谢。 “呀,我叫什么呢?嗯,说‘雷锋’太老土了。有了!”他故意顿了顿,眼里满是狡黠,“我叫‘春风’。呵呵……” 春日,细雨蒙蒙。我望着窗外如丝般的雨,发着呆。忽的,我的童年记忆像一缕春风拂面而来,将我带回童年时代……
小学语文教学论文 想象作文教学浅谈
小学语文教学论文:想象作文教学浅谈 作文是语文教学的重点,也是难点,而想像作文更是难中之难,小学生大都有“恐作症”,老师也常常为此头疼不已。那么怎样才能让学生在想象作文中有内容可写,有话可说呢?我认为可以从以下几方面训练。 一、观察现实生活,激发相关想象。 想像离不开现实,离开现实的想象是空洞的,无论哪一类想象作文都脱离不了现实生活。例如童话式想象作文,它是根据小学生喜爱动物的特点,用动物代替人类的形象来表达他们对世界的认识,在想像力作用下的动物附上了人的动作、语言、神态和思维。这类作文实际上是对现实的再现。 如想像作文“未来的×××”,这一类写未来生活的想象作文对学生而言有难度。未来是什么样的,学生除了接触到一些科幻片、科幻小说以外,其他的十分抽象,不知如何写。教师可引导学生仔细观察现实生活,展开想像的翅膀。例如现在的房屋,一旦完工,它便固定下来。如果让学生大但想象,让未来的建筑由一个个组装件构成,根据不同的需要进行不同的组合,这样既适合不同人的需求,又便于搬迁、移动,还可以维修,那该多好。又如当看到学校操场只有一处,空间过于狭小时,可以引导学生想象地下或空中操场,用电梯或升降机来回启用……这些现实中人们追求的更加便捷、完美的东西,都可以大胆想象它的样子、形状、功能。如果激发了学生想象的火花,那么展现在学生面前的空间不知有多大! 二、结合课文内容,进行再造想象。
课文是学生学习文化知识的重要材料,也是学生写作的典型范例。教师可充分利用课文资源,结合课文内容,让学生练习改写、续写、扩写等想象性作文,是一种行之有效的再造想象途径,能有效提高学生的想像能力。 例如《凡卡》一文,当凡卡满怀希望地把信寄出去后,爷爷能收到吗?爷爷在乡下会怎样想念凡卡呢?小凡卡后来的命运又会如何呢?让学生大胆去想象,续写出符合事情发展的故事,这样既加深了对课文内容的理解,又激活了学生想象的火花。 另外,还可以根据文中的插图进行补充或扩写。如《我的战友邱少云》一文在的插图,邱少云被烈火烧身时的巨大痛苦,是通过作者的心理活动侧面描写的,那么邱少云的心理感受会怎样呢?可引导学生观察他的神态、动作进行想象。 三、填补一些空白,设置整体形象。 在教学中选取一些相关的事物或词语,让学生进行整合,填补其中的空白,也是提高学生想象能力的重要手段。例如:画下几种不同的小动物,让学生按照自己的思维说出它们之间的关系,并想象出这些小动物之间会发生什么样的故事,然后进行口述表演,这样激起学生的童趣,他们的想象力就会更活跃。或者随便写下几个词语,让学生编上一段故事,用上这几个词语。这类填空白的训练,可以让学生的想象能力得到逐步提高。坚持长期训练,会收到意想不到的效果。 总之,学生作文能力的提高与教师的训练密不可分。我们应该在平时的作文教学中善动脑子,力求科学、有效,为学生作文插上想像的翅膀,让他们飞得更高、更远。
尊重议论文
谈如何尊重人尊重他人,我们赢得友谊;尊重他人,我们收获真诚;尊重他人,我们自己也 获得尊重;相互尊重,我们的社会才会更加和谐. ——题记 尊重是对他人的肯定,是对对方的友好与宽容。它是友谊的润滑剂,它是和谐的调节器, 它是我们须臾不可脱离的清新空气。“主席敬酒,岂敢岂敢?”“尊老敬贤,应该应该!”共和 国领袖对自己老师虚怀若谷,这是尊重;面对许光平女士,共和国总理大方的叫了一 声“婶婶”,这种和蔼可亲也是尊重。 尊重不仅会让人心情愉悦呼吸平顺,还可以改变陌生或尖锐的关系,廉颇和蔺相如便是 如此。将相和故事千古流芳:廉颇对蔺相如不满,处处使难,但蔺相如心怀大局,对廉颇相 当的尊重,最后也赢得了廉颇的真诚心,两人结为好友,共辅赵王,令强秦拿赵国一点办法 也没有。蔺相如与廉颇的互相尊重,令得将相和的故事千百年令无数后人膜拜。 现在,给大家举几个例子。在美国,一个颇有名望的富商在散步 时,遇到一个瘦弱的摆地摊卖旧书的年轻人,他缩着身子在寒风中啃着发霉的面包。富 商怜悯地将8美元塞到年轻人手中,头也不回地走了。没走多远,富商忽又返回,从地摊上 捡了两本旧书,并说:“对不起,我忘了取书。其实,您和我一样也是商人!”两年后,富商 应邀参加一个慈善募捐会时,一位年轻书商紧握着他的手,感激地说:“我一直以为我这一生 只有摆摊乞讨的命运,直到你亲口对我说,我和你一样都是商人,这才使我树立了自尊和自 信,从而创造了今天的业绩??”不难想像,没有那一 句尊重鼓励的话,这位富商当初即使给年轻人再多钱,年轻人也断不会出现人生的巨变, 这就是尊重的力量啊 可见尊重的量是多吗大。大家是不是觉得一个故事不精彩,不够明确尊重的力量,那再 来看下一个故事吧! 一家国际知名的大企业,在中国进行招聘,招聘的职位是该公司在中国的首席代表。经 过了异常激烈的竞争后,有五名年轻人,从几千名应聘者中脱颖而出。最后的胜出者,将是 这五个人中的一位。最后的考试是一场面试,考官们都 作文话题素材之为人处世篇:尊重 思路 人与人之间只有互相尊重才能友好相处 要让别人尊重自己,首先自己得尊重自己 尊重能减少人与人之间的摩擦 尊重需要理解和宽容 尊重也应坚持原则 尊重能促进社会成员之间的沟通 尊重别人的劳动成果 尊重能巩固友谊 尊重会使合作更愉快 和谐的社会需要彼此间的尊重 名言 施与人,但不要使对方有受施的感觉。帮助人,但给予对方最高的尊重。这是助人的艺 术,也是仁爱的情操。———刘墉 卑己而尊人是不好的,尊己而卑人也是不好的。———徐特立 知道他自己尊严的人,他就完全不能尊重别人的尊严。———席勒 真正伟大的人是不压制人也不受人压制的。———纪伯伦 草木是靠着上天的雨露滋长的,但是它们也敢仰望穹苍。———莎士比亚
最新一缕春风拂面来初三作文800字
【篇一】一缕春风拂面来初三作文800字 无论冬天怎样漫长,春天就如同樱花般总会熬过严冬,以最美的姿态绽放于枝头,与你相见。——题记 20XX年的冬天似乎格外漫长,一场突如其来的新冠肺炎疫情袭卷神州大地。原本热热闹闹的新年,突然变得冷冷清清,和煦的春风也被阻隔在口罩之外。 出于安全考虑,人与人之间时刻注意保持安全距离,每个人的微笑也被隐藏在口罩之中。有一天上完网课,有些疲惫的我抬头看向窗外,突然发现门前的那棵树居然长出了嫩芽。之前因为功课太繁忙,每天早出晚归,披星戴月,所以从未注意到窗前的那棵树。今年春天延迟开学,我在家里上网课,所以有幸能见证它的生长。 那些刚刚长出的幼小嫩叶簇拥在一起,就像一朵小小的绿色荷花。那绿就像被雨水冲洗过一般,即使身在火热的夏天,也能让你的心底泛起一阵清凉。生命有时很脆弱,也许一场大雨就能把这些嫩叶摧残,可生命又如此顽强,即使被暴雨摧残,它们依旧能够长出新芽,继续生长。我们人类又何尝不是这样呢? 也许无情的病毒会夺走我们的生命,但是我们有能力、有信心从死神手里抢回。在这场人与病毒的战争中,我们看不到硝烟四起,但每天都有生死离别,阴阳两隔。疫情发生以来,每个人都在全力为抗疫作贡献。你看,爱与希望总比死亡与病毒蔓延得更快,这就是生命的张力与尊严。回顾历史,人类经受过很多苦难,在苦难面前,生命是何等渺小,但我们从不放弃活下去的希望。即使在苦难中,我们也艰难地摸索前行,去等待属于我们的春天,去感受那春风拂面的温柔。 这个春天,即使我们遭受过挫折,但生命却不会因为这些挫折而停滞,相反,它会拼命生长,在苦难中开花、结果。我想每一个熬过冬天的种子都有一个春天的梦想。让我们再等等,等到这个春天真正的到来,等到所有的花儿都开放,等到看樱花的人比樱花还要多,等到和煦的春风又再次抚摸脸颊。我们一定会摘下口罩,微笑问好。 【篇二】一缕春风拂面来初三作文800字 春风拂面,在其他任何季节,也会有一番如沐春风的舒畅与感动。 冬,一个寒冷的冬日,呼呼的寒风猛烈地刮着,呵气成冰的天气让我倍感不适,我因病体育课时在班中休息,听着外面强烈的风声,望着自己已冻得通红甚至有些僵硬的手,不禁一阵猛搓。这是,老师轻轻推开了门走了进来,端来一杯热水,关切的问道:“感觉好些了吗?喝点水,暖暖身子,如果不舒服直接去办公室打电话啊,不用找我。”我点点头,喝着水,感到无比的暖意,在这寒冬,我有一份感动,如同春风拂面。 不仅是在冬日,在夏日,也会有春风拂面的感觉。
【部编人教版】最新版语文六年级上册-小学分类作文全攻略之怎样写好想象类作文
小学分类作文全攻略之怎样写好想象类作文未来因为不可预知而显得神秘莫测,令人神往;想象,因为未能定格而让人激情膨胀。当我们置身于高科技时代,我们其实就是在不断地享受着人类的创造之果给我们的生活带来的舒适、方便与快捷。人类社会,在想象中不断完善,在创造中走向壮大。 <一>想象 1.定义:想象是人在头脑里对已储存的表象进行加工改造形成新形象的心理过程。想象作文与平时作文中的“想象”有所不同。如写桃花,可根据桃花的形想象它像一颗颗五角星,根据它盛开的样子想象它像小姑娘绽开的笑脸,这样就可以把桃花这个事物写具体生动。以上例子只能说是平时作文中一个想象的小节,并不代表它就是想象作文,想象作文不是细节和局部情节的想象,而是整篇作文的想象。 2.想象的分类 (1)再造想象含义:根据别人的描述或图样,在头脑中形成新形象的过程。意义:使人能超越个人狭隘的经验范围和时空限制,获得更多的知识;使我们更好理解抽象的知识,使之变得具体、生动、易于掌握。 形成正确再造想象的基本条件:一是能正确理解词与符号、图样标志的意义;二是有丰富的表象储备。 (2)创造想象含义:不根据现成的描述,而在大脑中独立地产生新形象的过程。创造想象的特殊形式——幻想:与个人生活愿望相联系并指向未来的想象。两个特点:体现了个人的憧憬或寄托,不与当前的行动直接联系而指向于未来。具有积极意义:积极的幻想是创造力实现的必要条件,是科学预见的一部分;是激励人们创造的重要精神力量;是个人和社会存在与发展的精神支柱。 <二>想象类作文的分类: 【1】童话 童话写作时,首先要有一定的故事情节,在设计情节时不要太复杂,可采用拟人的手法,把物当做人来写,让物具有人的思想感情。其次要充分发挥想象,把生活中本质的事物,通过想象编成趣味性的故事,展现在读者面前。再次要注意想象与现实生活的联系。现实生活时想象的基础,通过艺术加工后,表达一种
2017-2018福州格致中学高一上期中试卷
试卷第1页,总5页 福州格致中学2017-2018学年第一学段 高一物理检测 命题题:林枝钦 审核:王宇 日期:2017.11.7 (完卷时间:70分钟 全卷满分:100分) 一.选择题(每题4分,共40分,其中1-6题为单项选择,7-10题为多项选择;多项选择选全对得4分,选不全得2分,错选不得分) 1.下列各组物理量中全部是矢量的是( ) A .位移、时间、速度、加速度 B .速度、平均速度、位移、加速度 C .质量、路程、速度、平均速度 D .位移、路程、时间、加速度 2.下面几组力中,可能成为平衡力的有( ) A .3N 、4N 、8N B .2N 、5N 、9N C .4N 、6N 、8N 、12N D .7N 、6N 、12N 、26N 3.一物体由某一高度做自由落体运动,第1s 内下降的高度是总高度的1/16,g=10m/s 2,则( ) A .物体下落的高度为5m B .物体下落的高度为25m C .物体下落的高度为45m D .物体下落的高度为80m 4.一个光滑的圆球搁在光滑斜面和光滑的竖直挡板之间,如图.当竖直挡板由竖直逆时针转到由图示虚线位置至水平位置过程中,则圆球受到的弹力( ) A .斜面对圆球的弹力先变小后变大 B .斜面对圆球的弹力逐渐变大 C .挡板对圆球的弹力先变小后变大 D .挡板对圆球的弹力逐渐变小 5.如图所示,两个质量均为m 的物体分别挂在支架上的B 点(如图甲所示)和跨过滑轮的轻绳BC 上(如图乙所示),图甲中轻杆AB 可绕A 点转动,图乙中水平轻杆一端A 插在墙壁内,已知θ=30°,则图甲中轻杆AB 受到绳子的作用力F 1和图乙中滑轮受到绳子的作用力F 2分别为( ) A .F 1=mg 、F 2= mg B .F 1= mg 、F 2=mg C .F 1= mg 、F 2=mg D .F 1= mg 、F 2=mg
相关文档
- 2015-2016学年高一英语上学期期末考试试题
- 2020学年高一英语上学期期末考试试题(新版)新人教版
- 江西省鹰潭市高一英语上学期期末考试试题新人教版
- 部编版2020学年高一英语上学期期末考试试题(无答案)(新版) 新人教版(1)
- 2019年高一英语上学期期末考试试卷新人教版.
- 新人教版高一英语上学期期末试卷及答案
- 2019-2020最新高一英语上学期期末考试试题A卷
- 最新高一英语上学期期末测试题(含答案)
- 最新高一上学期期末考试英语试卷
- 人教版高一上学期英语期末测试题(含答案)
- 高一英语上学期期末测试题(含答案)
- 高一英语上学期期中试题(新版)新人教版
- 高一英语上学期期末考试试题(新版)新人教版
- 最新高一英语上学期期末考试试卷含答案
- 2019-2020最新高一英语上学期期末考试试题
- 最新高一上学期期末考试英语试卷
- 2019年高一英语上学期期末联考试题.
- 高一英语上学期期末考试试题
- 最新高一英语上学期期末考试试题 (10)
- 高一英语上学期期末模拟试题(新版)新 人教版
